Summary
This box is quite interesting, in the sense that once you have rooted the box, you are actually not quite done. You first need to recover the flag, which was accidentally deleted. A very interesting concept and a unique way to add a forensics challenge to the box.
Foothold
We start out by doing a nmap port scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(bitis㉿workstation)-[~/htb/Machines/mirai]
└─$ nmap -sC -sV 10.129.83.20
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-25 00:55 CEST
Nmap scan report for 10.129.83.20
Host is up (0.076s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
| ssh-hostkey:
| 1024 aa:ef:5c:e0:8e:86:97:82:47:ff:4a:e5:40:18:90:c5 (DSA)
| 2048 e8:c1:9d:c5:43:ab:fe:61:23:3b:d7:e4:af:9b:74:18 (RSA)
| 256 b6:a0:78:38:d0:c8:10:94:8b:44:b2:ea:a0:17:42:2b (ECDSA)
|_ 256 4d:68:40:f7:20:c4:e5:52:80:7a:44:38:b8:a2:a7:52 (ED25519)
53/tcp open domain dnsmasq 2.76
| dns-nsid:
|_ bind.version: dnsmasq-2.76
80/tcp open http lighttpd 1.4.35
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: lighttpd/1.4.35
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.16 seconds
Three ports are open on the machine, port 22, 80 and 53 which is hosting a Domain Name Service. If we try to visit the web application, we just get greeted with a blank page. Scanning the application with gobuster reveals the following:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(bitis㉿workstation)-[~/htb/Machines/mirai]
└─$ gobuster dir -u 10.129.83.20 -w /usr/share/wordlists/SecLists/Discovery/Web-Content/raft-small-words.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.83.20
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/raft-small-words.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/06/25 01:00:11 Starting gobuster in directory enumeration mode
===============================================================
/admin (Status: 301) [Size: 0] [--> http://10.129.83.20/admin/]
/.js (Status: 200) [Size: 61]
/versions (Status: 200) [Size: 18]
/.min.js (Status: 200) [Size: 61]
/.inc.js (Status: 200) [Size: 61]
/.3.2.min.js (Status: 200) [Size: 61]
===============================================================
2022/06/25 01:04:16 Finished
===============================================================
If we visit /admin we are lead to the pi-hole admin console.
 The pi-hole admin console
The pi-hole admin console
We can then attempt to login.
If we attempt the default credentials pi:raspberry on the admin console we fail to login, however we can actually ssh into the machine with these credentials.
Privilege escalation
Running sudo -l reveals that we have complete access to sudo, so becoming root is as simple as running sudo su - or simply su -
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
pi@raspberrypi:~ $ sudo -l
Matching Defaults entries for pi on localhost:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User pi may run the following commands on localhost:
(ALL : ALL) ALL
(ALL) NOPASSWD: ALL
pi@raspberrypi:~ $ su -
Password:
SSH is enabled and the default password for the 'pi' user has not been changed.
This is a security risk - please login as the 'pi' user and type 'passwd' to set a new password.
SSH is enabled and the default password for the 'pi' user has not been changed.
This is a security risk - please login as the 'pi' user and type 'passwd' to set a new password.
root@raspberrypi:~#
Rooted! Or not? Reading root.txt reveals that the flag has been moved:
1
2
root@raspberrypi:~# cat root.txt
I lost my original root.txt! I think I may have a backup on my USB stick...
Using df we can see filesystems as well as where they are mounted on the system.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
Filesystem 1K-blocks Used Available Use% Mounted on
aufs 8856504 2835676 5547896 34% /
tmpfs 102396 4884 97512 5% /run
/dev/sda1 1354528 1354528 0 100% /lib/live/mount/persistence/sda1
/dev/loop0 1267456 1267456 0 100% /lib/live/mount/rootfs/filesystem.squashfs
tmpfs 255988 0 255988 0% /lib/live/mount/overlay
/dev/sda2 8856504 2835676 5547896 34% /lib/live/mount/persistence/sda2
devtmpfs 10240 0 10240 0% /dev
tmpfs 255988 8 255980 1% /dev/shm
tmpfs 5120 4 5116 1% /run/lock
tmpfs 255988 0 255988 0% /sys/fs/cgroup
tmpfs 255988 8 255980 1% /tmp
/dev/sdb 8887 93 8078 2% /media/usbstick
tmpfs 51200 0 51200 0% /run/user/999
tmpfs 51200 0 51200 0% /run/user/1000
If we go to /media/usbstick we find this message from James:
1
2
3
4
5
6
7
root@raspberrypi:/media/usbstick# ls
damnit.txt lost+found
root@raspberrypi:/media/usbstick# cat damnit.txt
Damnit! Sorry man I accidentally deleted your files off the USB stick.
Do you know if there is any way to get them back?
-James
We can use dcfldd on the target machine to make a copy of the filesystem, which we can then coy to our system via scp.
1
2
3
4
5
root@raspberrypi:/home/pi# dcfldd if=/dev/sdb of=/home/pi/usb2
256 blocks (8Mb) written.
320+0 records in
320+0 records out
root@raspberrypi:/home/pi#
We can then run testdisk on it.
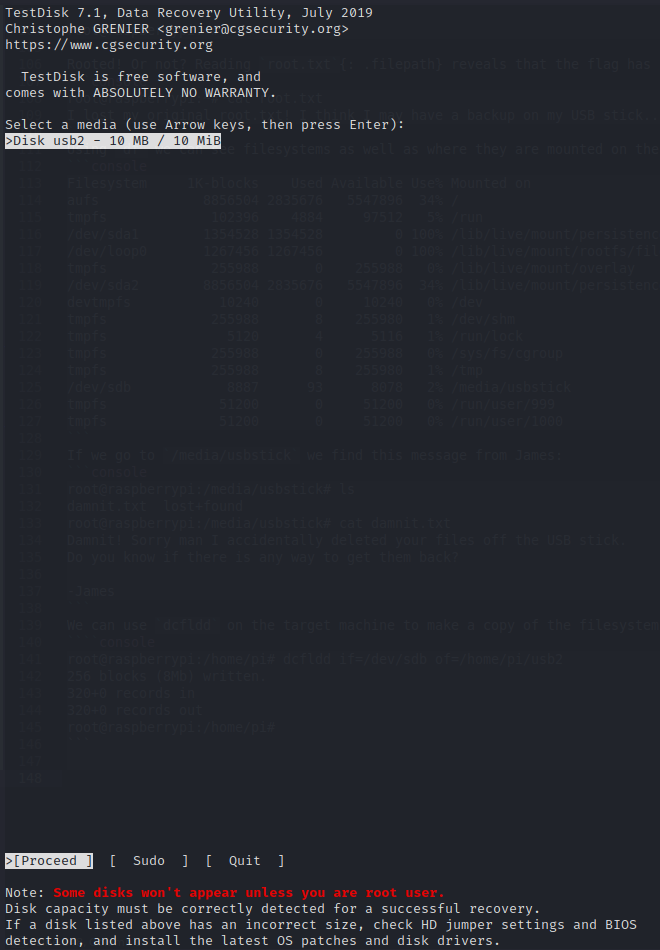
We then select the disk we want to test, the partition table type and list partition. I simply selected None as partition type. We can then see the contents of the partition.
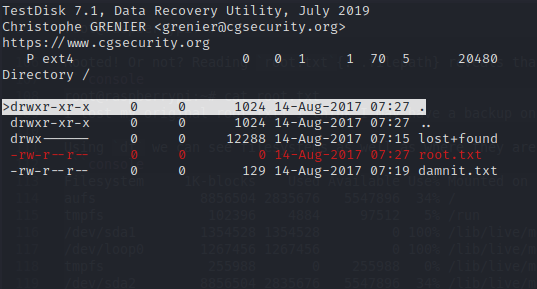
Testdisk finds root.txt on the partition, however if we copy the file with testdisk we get an empty file out. However since the file is clearly present somewhere on the filesystem, we can run strings on it and hopefully recover some of the data.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(bitis㉿workstation)-[~/htb/Machines/mirai]
└─$ strings usb2
>r &
/media/usbstick
lost+found
root.txt
damnit.txt
>r &
>r &
/media/usbstick
lost+found
root.txt
damnit.txt
>r &
/media/usbstick
2]8^
lost+found
root.txt
damnit.txt
>r &
3d3e483143ff12ec505d026fa13e020b
Damnit! Sorry man I accidentally deleted your files off the USB stick.
Do you know if there is any way to get them back?
-James
Luckily the output of strings gives us the root flag, and we have finally rooted the machine!

