Description
This app has stored my credentials and I can only login automatically. I tried to intercept the login request and restore my password, but this seems to be a secure connection. Can you help bypass this security restriction and intercept the password in plaintext?
Setup and flag
I used genymotion to emulate an android device.
Install necessary tools with the commands
1
2
3
pip install Frida
pip install objection
pip install frida-tools
Connect to the emulater via adb, this can be done with the commands adb devices and adb connect IP:PORT check architechture with the command:
1
2
3
┌──(bitis㉿workstation)-[~/htb/challenges/android/pinned]
└─$ adb shell getprop ro.product.cpu.abi
x86
Download the corresponding frida server from this link, and then push it to the device with the following command:
1
adb push frida-server-15.1.28-android-x86 /data/local/tmp
and then give permissions to the server with the command
1
adb shell chmod 777 /data/local/tmp/frida-server-15.1.28-android-x86
Get the burpsuite certificate by visiting http://burpsuite/ in a browser where the burpsuite proxy is active. The certificate is then pushed to the device with the following command:
1
adb push cacert.der /data/local/tmp/cert-der.crt
The reason for the specific name is that the injection script is looking for a file with that specific name. We also need to ensure that burpsuite is ready to intercept the traffic coming from the android device, and that the android is routing its’ traffic through the proxy. This is done by entering wifi options on the emulater, checking manual proxy configuration and then entering the IP of the device hosting the emulater and the port that burpsuite is listening on. I also set it to listen on a specific port as well as all interfaces.
The script is then pushed to the device and run with the following commands:
1
2
adb push C:\ADB\fridascript.js /data/local/tmp
adb shell /data/local/tmp/frida-server &
Once the server is running we can list all running processes with frida-ps -U.
I then injected the script with the command frida -U -p 2599 -l fridascript.js --no-paus
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(bitis㉿workstation)-[~/htb/challenges/android/pinned]
└─$ adb shell /data/local/tmp/frida-server-15.1.28-android-x86 &
[1] 4360
┌──(bitis㉿workstation)-[~/htb/challenges/android/pinned]
└─$ frida -U -p 2112 -l fridascript.js --no-paus 1 ⚙
____
/ _ | Frida 15.1.28 - A world-class dynamic instrumentation toolkit
| (_| |
> _ | Commands:
/_/ |_| help -> Displays the help system
. . . . object? -> Display information about 'object'
. . . . exit/quit -> Exit
. . . .
. . . . More info at https://frida.re/docs/home/
. . . .
. . . . Connected to Google Pixel 3 (id=192.168.57.103:5555)
Attaching...
[.] Cert Pinning Bypass/Re-Pinning
[+] Loading our CA...
[o] Our CA Info: CN=PortSwigger CA, OU=PortSwigger CA, O=PortSwigger, L=PortSwigger, ST=PortSwigger, C=PortSwigger
[+] Creating a KeyStore for our CA...
[+] Creating a TrustManager that trusts the CA in our KeyStore...
[+] Our TrustManager is ready...
[+] Hijacking SSLContext methods now...
[-] Waiting for the app to invoke SSLContext.init()...
[Google Pixel 3::PID::2112 ]->
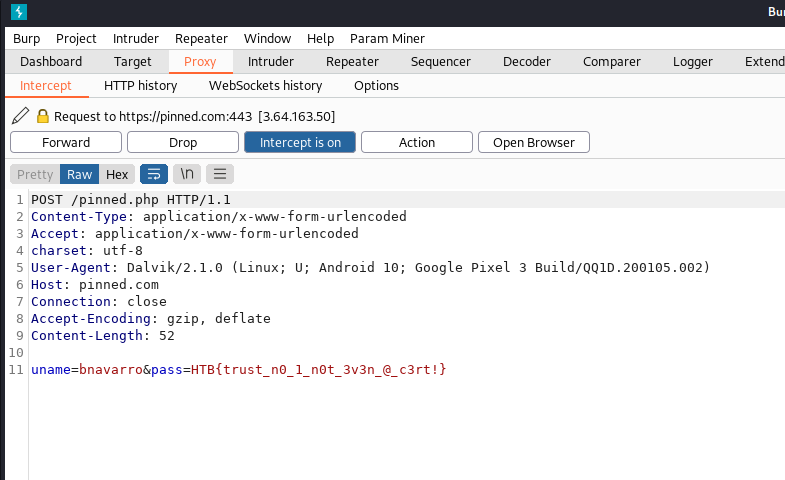
We can then view the traffic in burpsuite: